涉及到的题目链接:链接:https://pan.baidu.com/s/1ll1bWhd845tj6JDFkx3i6Q
提取码:fsrp
Web Awesome
打开网页,看到提交按钮的事件
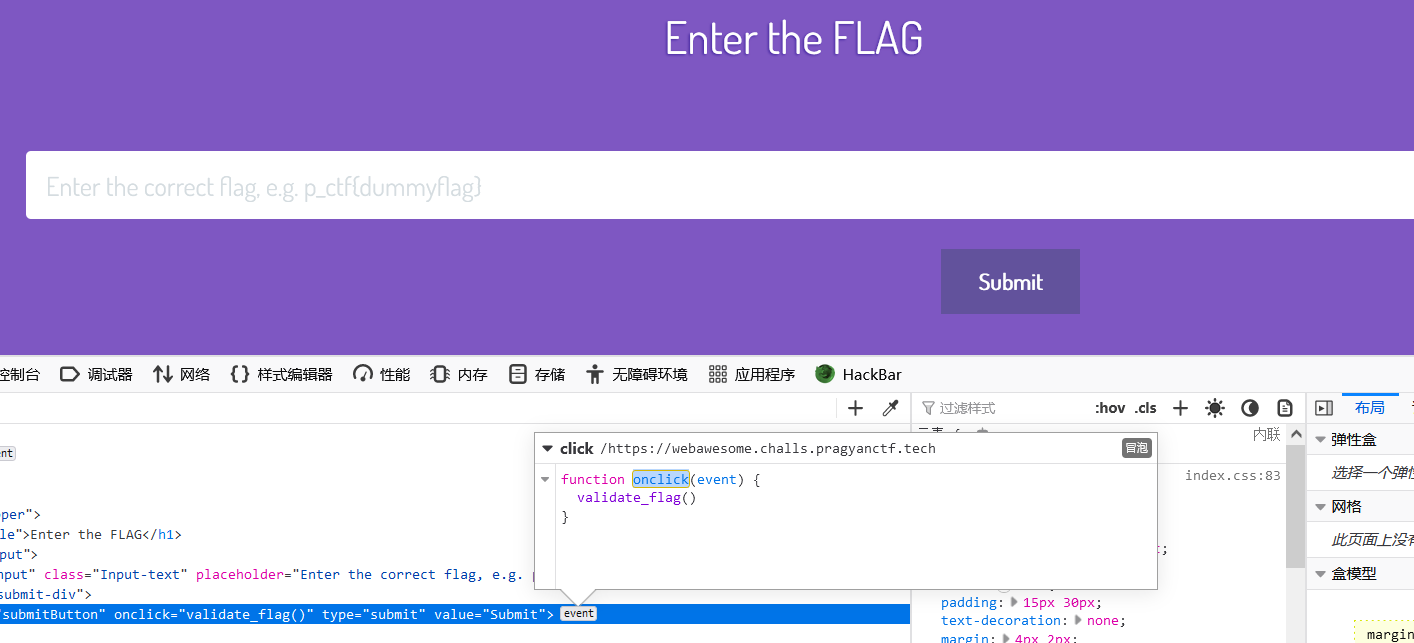
从源代码中定位到这个onclick
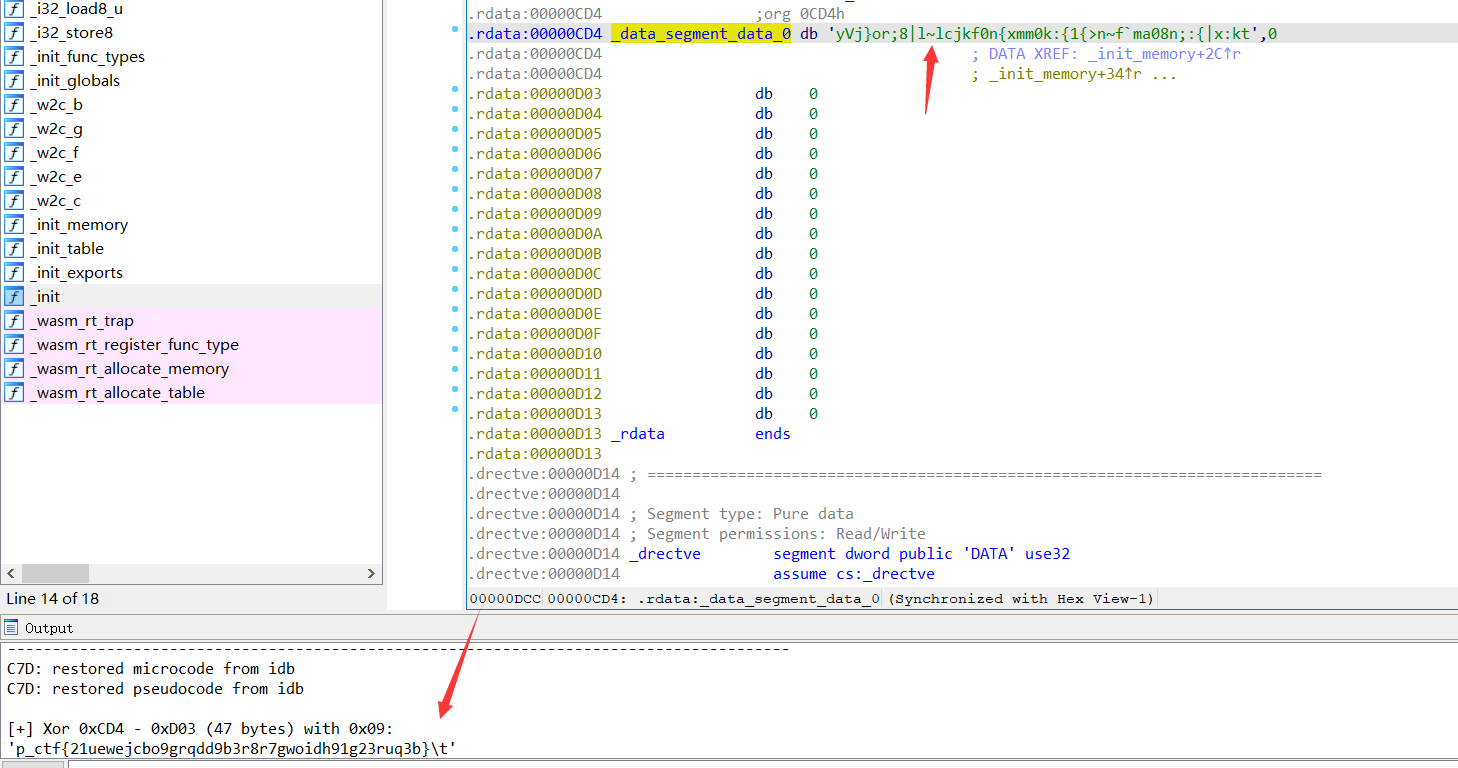
这是一个考察wasm的题,将网站中的index.wasm下载下来,进行.wasm->.o的转换,ida中看到转化后的目标文件,运算只有一个异或9
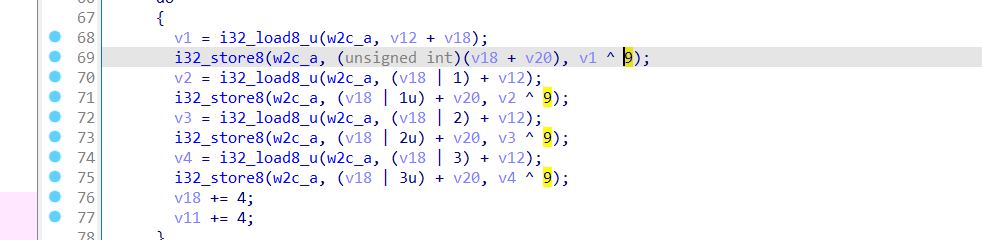
再看到init_memory中的数据,异或一下9即是flag
Oak
给的一个class文件,使用jar命令将这个class文件打包成一个jar包,然后用jd-gui查看jar包。
1 | jar -cvf Oak.jar Oak.class |
jar包内容如下,剩下就是简单的java代码审计逆向。
1 | import java.io.PrintStream; |
Secure-lock
开始就是五个逻辑很明显的check
1、check1
限定了这个数是45位,且给了这个数的后15位与前9位,而check_num2就是验证这个数是否是阿姆斯特朗数。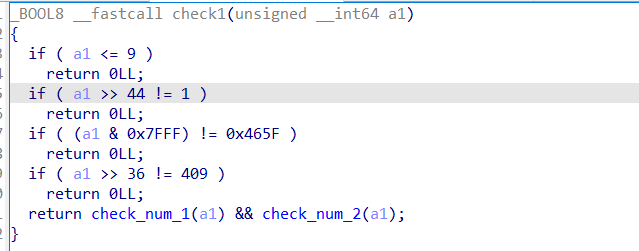
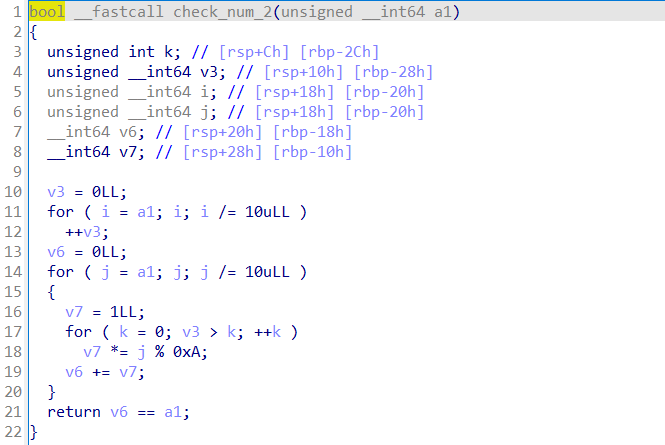
因此这个checK就是让我们求一个45位,且限定了前9位与后15位的阿姆斯特朗数,我们爆破中间21位即可。
1 | check = lambda N:sum(map(lambda x: int(x)**len(str(N)), str(N))) == N |
2、check2
一个6字节伪随机数,与shuffle算法,这里要注意一下的就是通过输入8字节数据通过shuffle函数后要变为6字节与伪随机数相等。
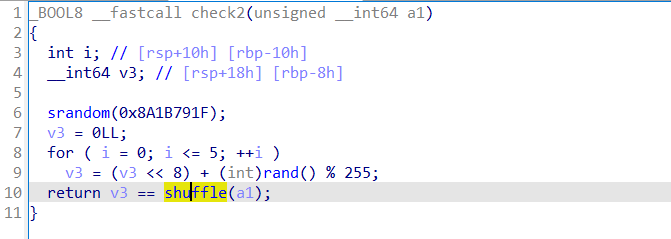
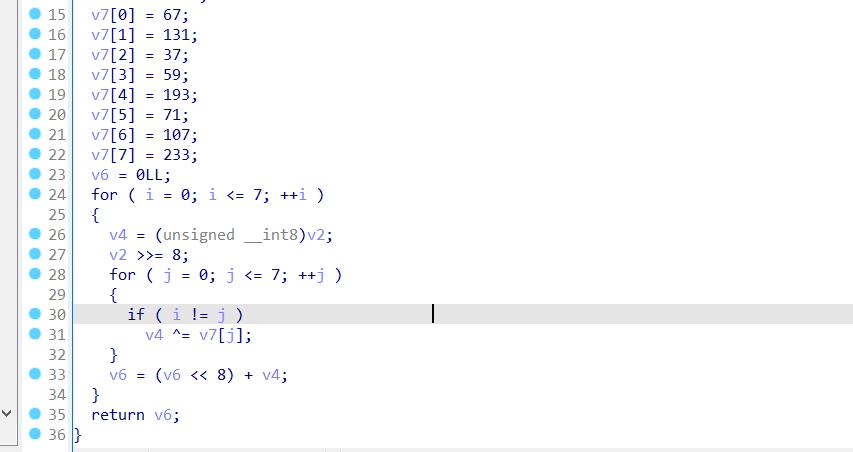
解密:
1 | v7 = [0]*8 |
3、check3
一个base64
4、check4
多个方程: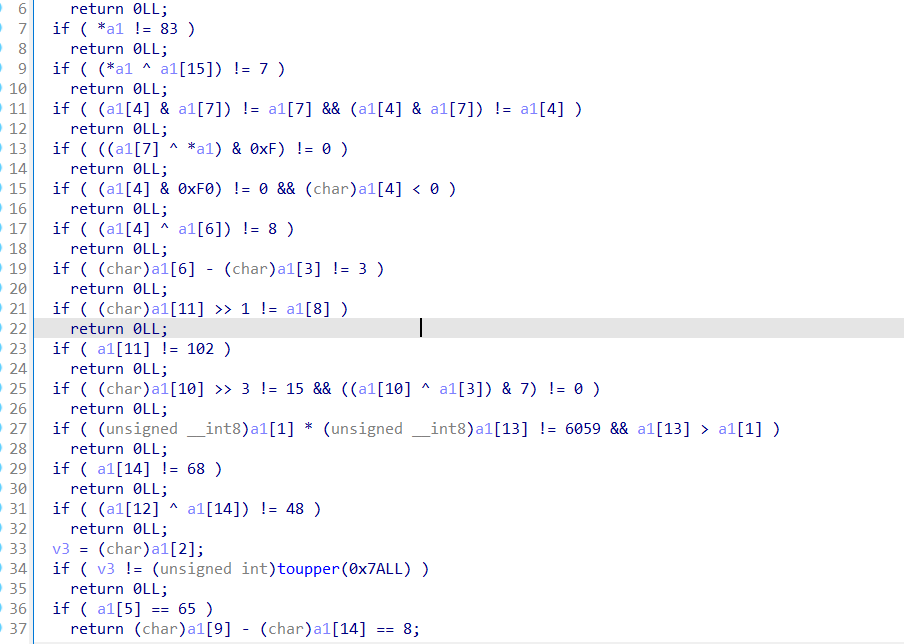
因为这个check的有一个条件 && ,反过来就是 || 这样就导致了多解,这使得这个程序本地有多个可以反馈正确的输入。
z3解即可。
5、check5
就是一些异或和移位算法:
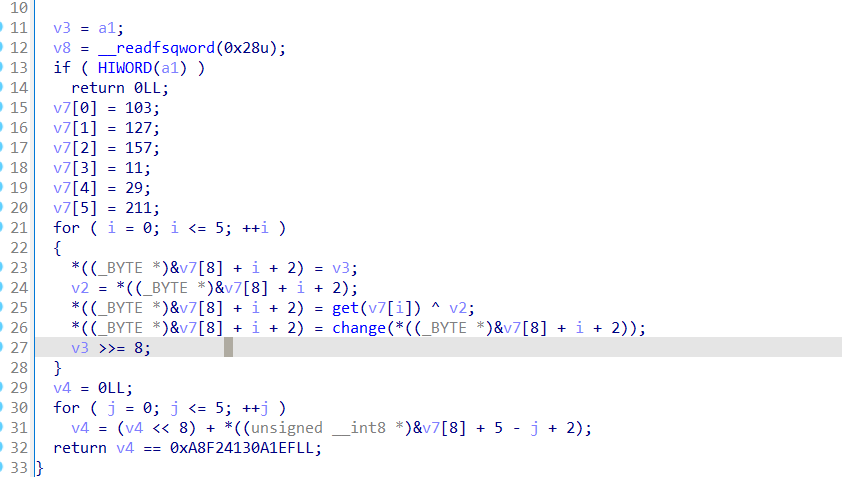
解密:
先跑出get()函数返回的数据:
1 |
|
异或和移位解密:
1 | x = [0x39, 0xcf, 0xa1, 0x25, 0x71, 0x15] |
过了5个check后来看到最后的check_flag,就是将前5个check输入的数据作为key和flag进行一些异或运算
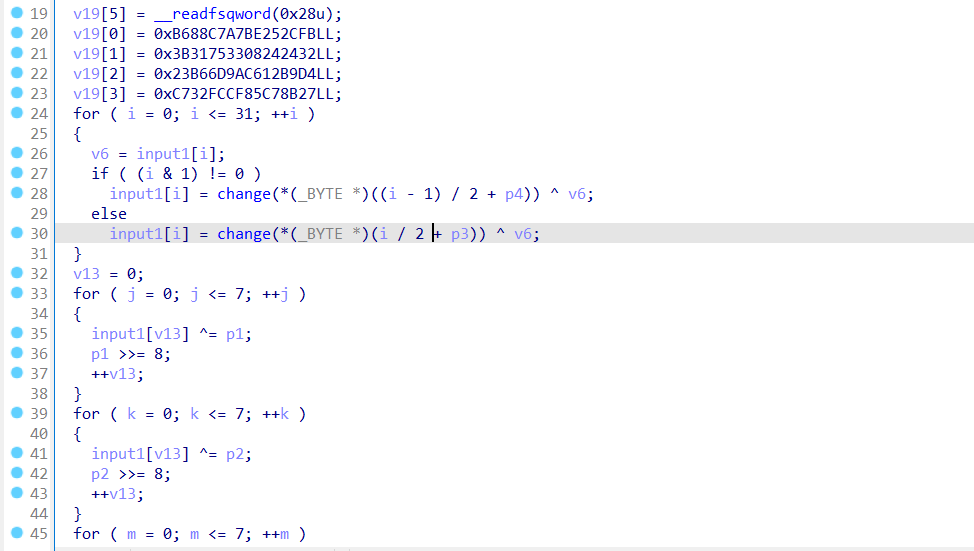
总结一下,得到前5个check的输入和最后的密文如下: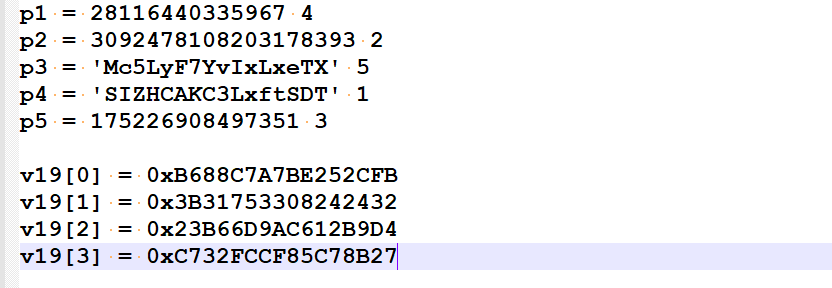
解密:
以下涉及到一个python中将一个多元列表转化为一元列表的简单写法:
1 | a = [j for i in aa for j in i] |
1 | v19[0] = 0xB688C7A7BE252CFB |
p_ctf{L2<I_w4qN%t_$3CurE_3nOuGH}
Classic
ida中打开所给elf文件,很明显这不是一个常规的elf文件,从字符串我们能知道这是一个python文件打包成的elf文件。
使用archive_viewer.py对该elf文件进行解包
archive_viewer.py就在我们安装pyinstaller包的子目录下,如下面截图中的路径
pyinstaller的安装:pip3 install pyinstaller
找到archive_viewer.py的位置后将其复制到当前要解包elf文件所在的目录:
解包:
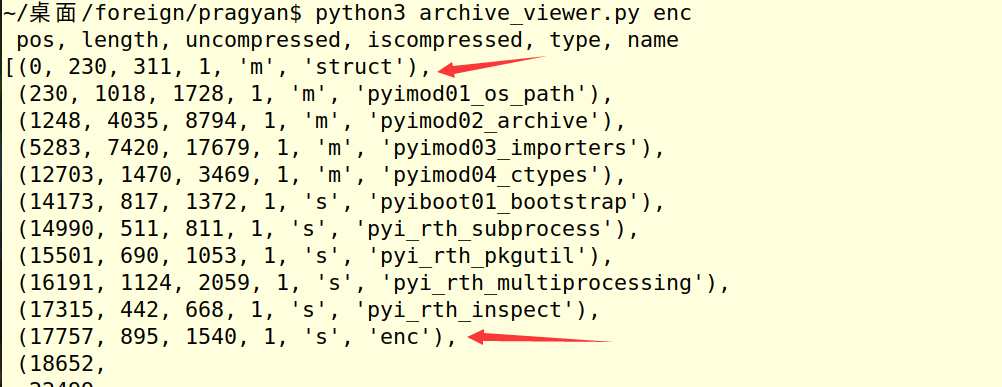
使用 x 命令提取出enc与struct文件:
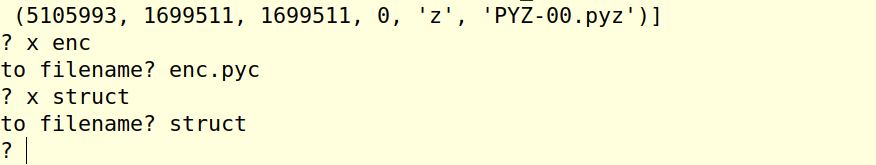
接着就是常规的修复pyc头,然后使用uncompyl6对修复后的pyc文件进行反编译即可。
看到得到的py文件:
1 | # uncompyle6 version 3.7.4 |
然后我们看到题目所给的另外一个.enc密文文件:
1 | 25 46 -3 73 4 86 5 52 -2 86 6 48 3 88 91 2 25 53 -2 55 -2 -1 0 53 87 0 6 -2 85 52 0 2 88 89 5 73 3 -3 2 1 -6 25 4 83 0 48 0 89 4 48 25 88 89 4 6 55 -1 7 1 1 25 1 85 53 6 1 87 7 0 3 86 136 6 3 2 42 4 42 -1 50 7 86 2 25 -4 138 3 48 25 136 90 6 25 4 1 3 0 -9 25 6 89 55 2 -6 87 4 0 50 84 137 4 5 |
看到所给的.enc密文文件会感觉莫名奇妙,也不清楚他们到底对应原py代码中的那个变量,这也是本题很谜语的地方,还有就是根本不知道原py代码中那个变量是我们要逆的flag。
经过梳理分析,得到正确的考点和逻辑如下:
1.密文文件中所给的数组为py代码中的 x 数组
2.密文文件中的encrypted key为py代码中的 k2
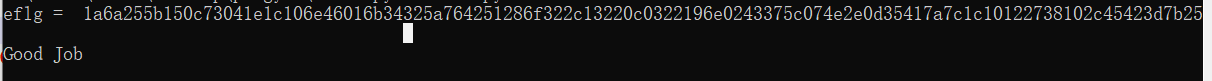
3.py代码中的eflg变量与enc变量是相同的含义(再py代码中根本没体现出来,故意的吗,,,
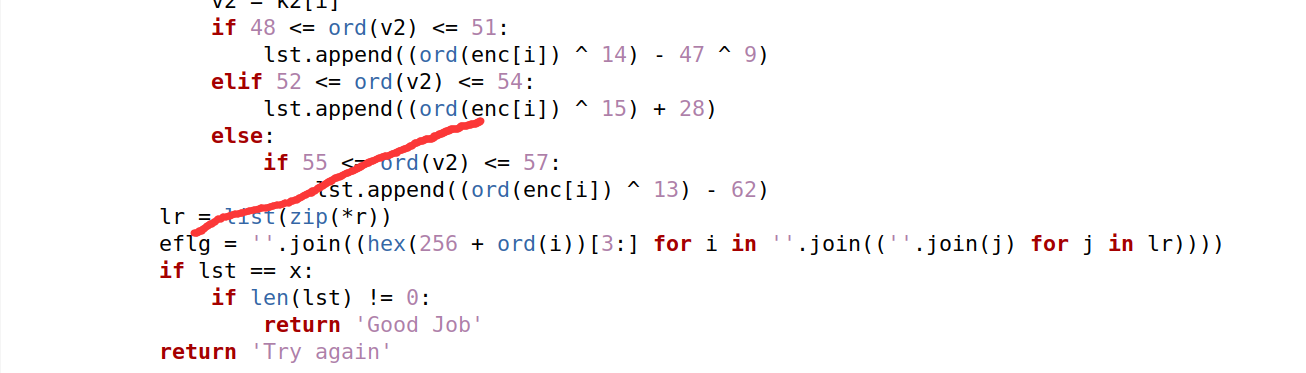
4.知道以上三点后,可以知道本题目的加密算法是:a变量是flag,经过a1密钥加密最后得到eflg,而eflg也是对应enc,而x变量是enc加密的值。
因此本题就是要我们通过加密flag的加密值和加密的密钥值来先求出加密的flag和密钥,最后通过密钥解密出加密的flag。
解密:
1.利用加密的密钥解密出加密的flag
1 | def d1(): |
2.根据flag的格式 p_ctf{ 与加密的密钥还原出正确的密钥
1 | a = 'p_ctf{' |
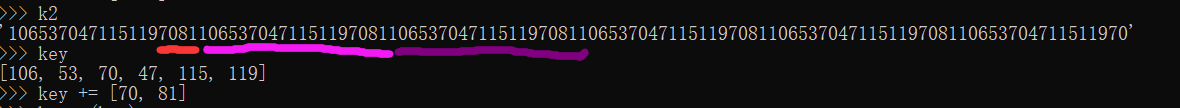
3.使用密钥解密还原出flag
1 | key = list(b'j5F/swFQ') |