Re
apacha
考了一个xxtea加密算法:key是{1, 2, 3, 4}
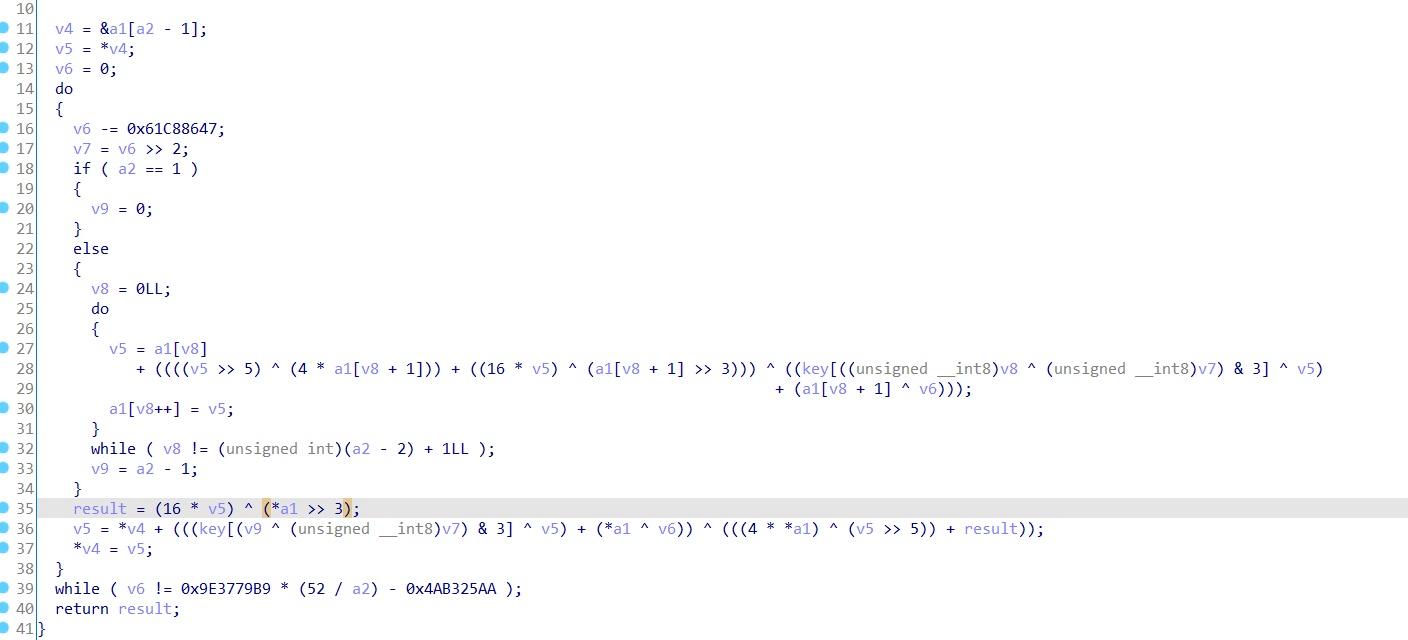
跟着算法逻辑逆一下就行了:
1 |
|
helloRe
就是一个异或解密,但是可以从这里学习一下STL模板中的string的结构。
能猜测出v14就是我们输入字符串的长度,但是怎么来的呢?其实使用了string结构。
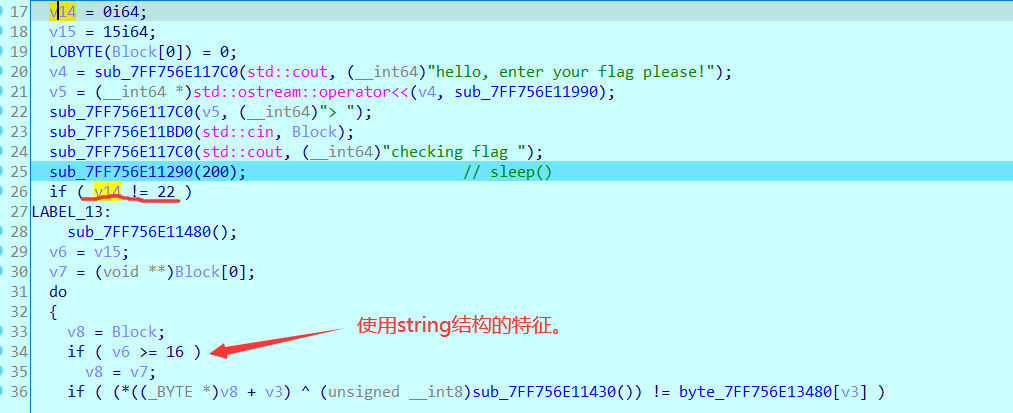
string结构:一共占24个字节(这也是一个可以让我们用来识别的特征)
1 | struct string |
来测试一个输入看看:
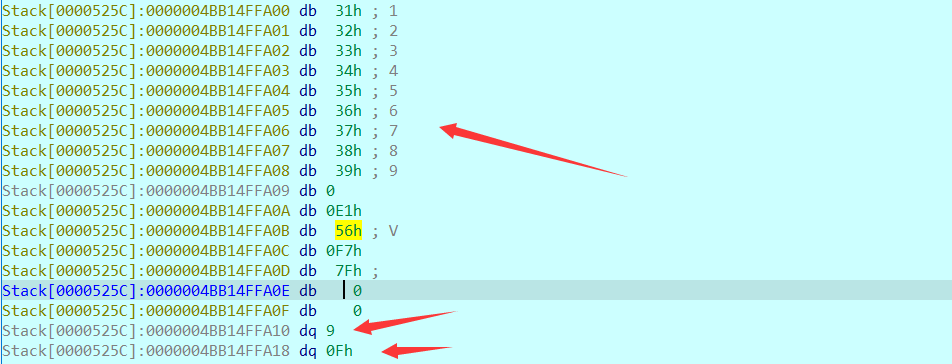
最后题解:
1 | from ida_bytes import * |
pypy
给了通过dis模块得到的python反汇编代码,我把对应的python代码注释了下:
1 | 4 0 LOAD_GLOBAL 0 (input) |
最后简单逆一下:
1 | enc = '30466633346f59213b4139794520572b45514d61583151576638643a' |
ezApk
简单的安卓,只有java代码,找到按钮活动。
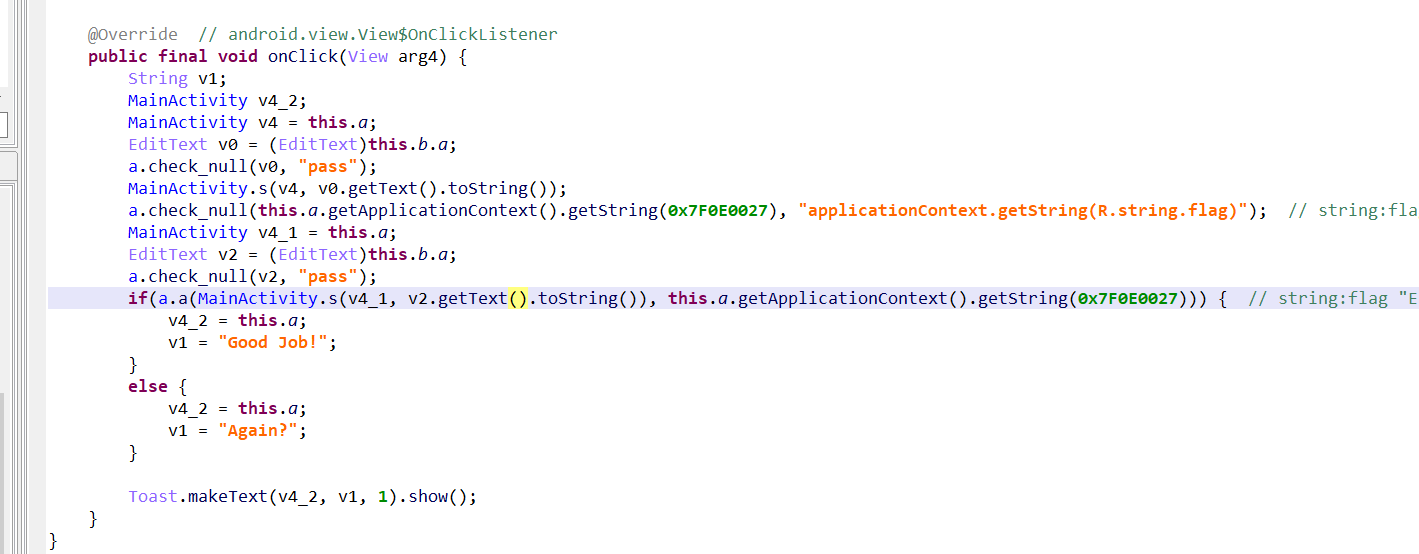
就是取出文本内容,然后把输入和密文传入s方法,验证是否正确。
到s方法:一个cbc模式的aes加密,填充方式为PKCS7Padding。
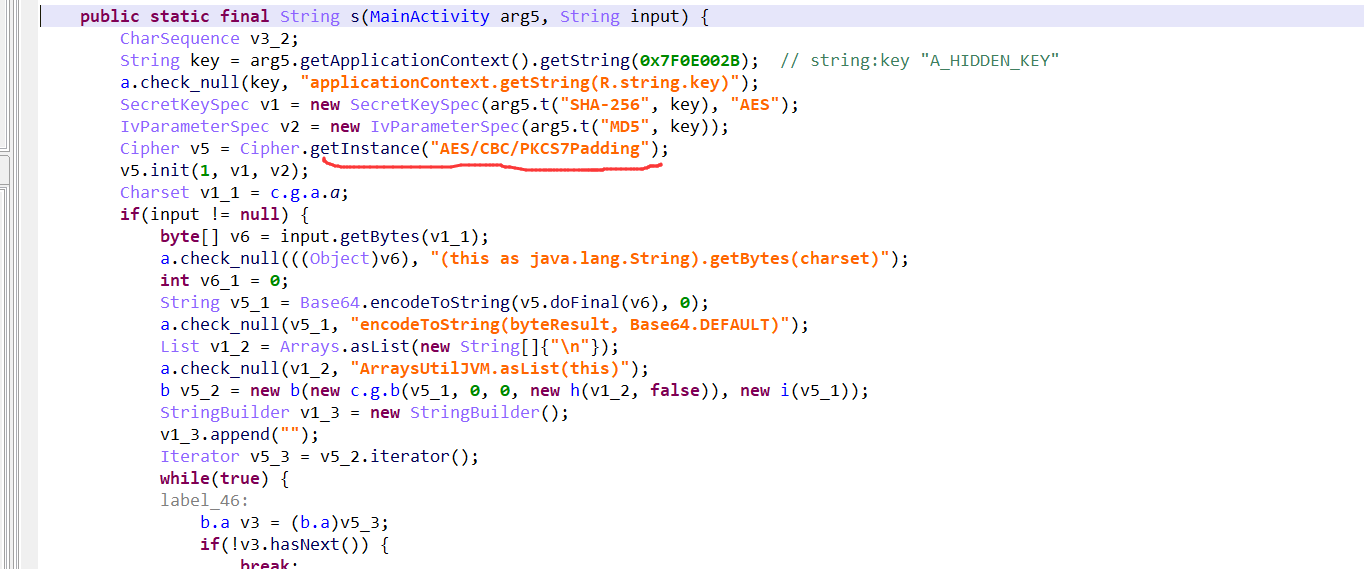
所以解密密文就应该是flag了,使用java用同样的方式调用一下解密方法。这里注意一点就是:java中自带的是PKCS5Padding填充,直接使用PKCS7Padding会报错,但搜索到这2个使用起来是一样的,就直接改成PKCS5Padding就好了。
1 | package ctf; |
其实也不用这么麻烦的,关键是想练习一下java。
自己算一下hash得到的key和iv用python或者在线网站解密一下,方便的多。
1 | #coding:utf-8 |
helloRe2
首先输入pass1的逻辑,转化一个128位的大数与指定大数比较,然后以挂起创建自身进程的子进程,调用CreateFileMappingA()函数把文件映像到内存,再使用MapViewOfFile()函数把文件视映像到进程地址空间上(用于把当前进程的内存空间的数据与子进程共享),然后在非调试状态下对要共享的数据简单的异或加密一下,最后恢复启动刚刚创建的子进程,自身进程睡眠挂起:
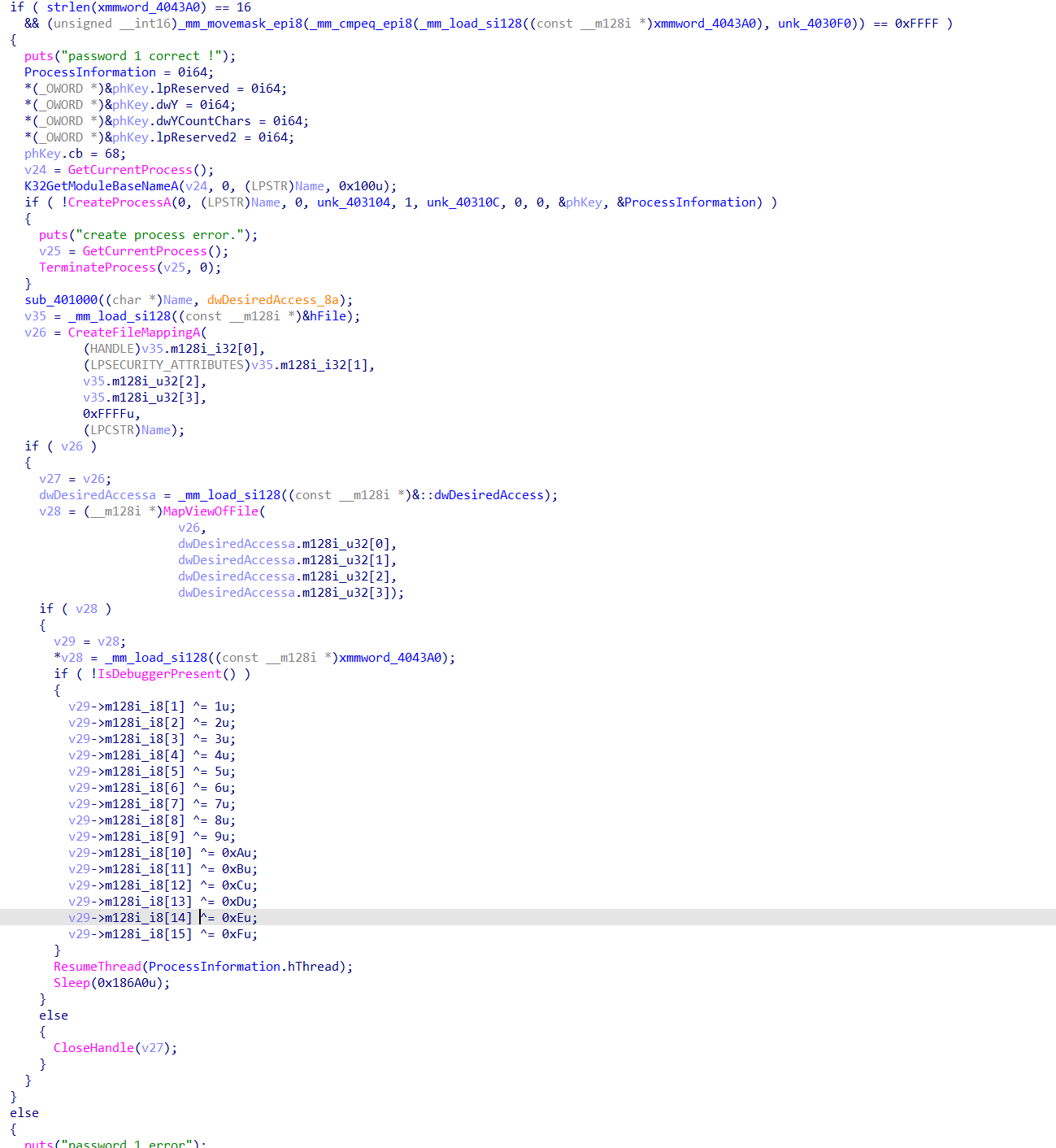
子进程启动后,调用OpenFileMappingA()与MapViewOfFile()查看父进程共享的内存数据,若存在则调用输入pass2的逻辑,然后一个cbc模式的aes加密。
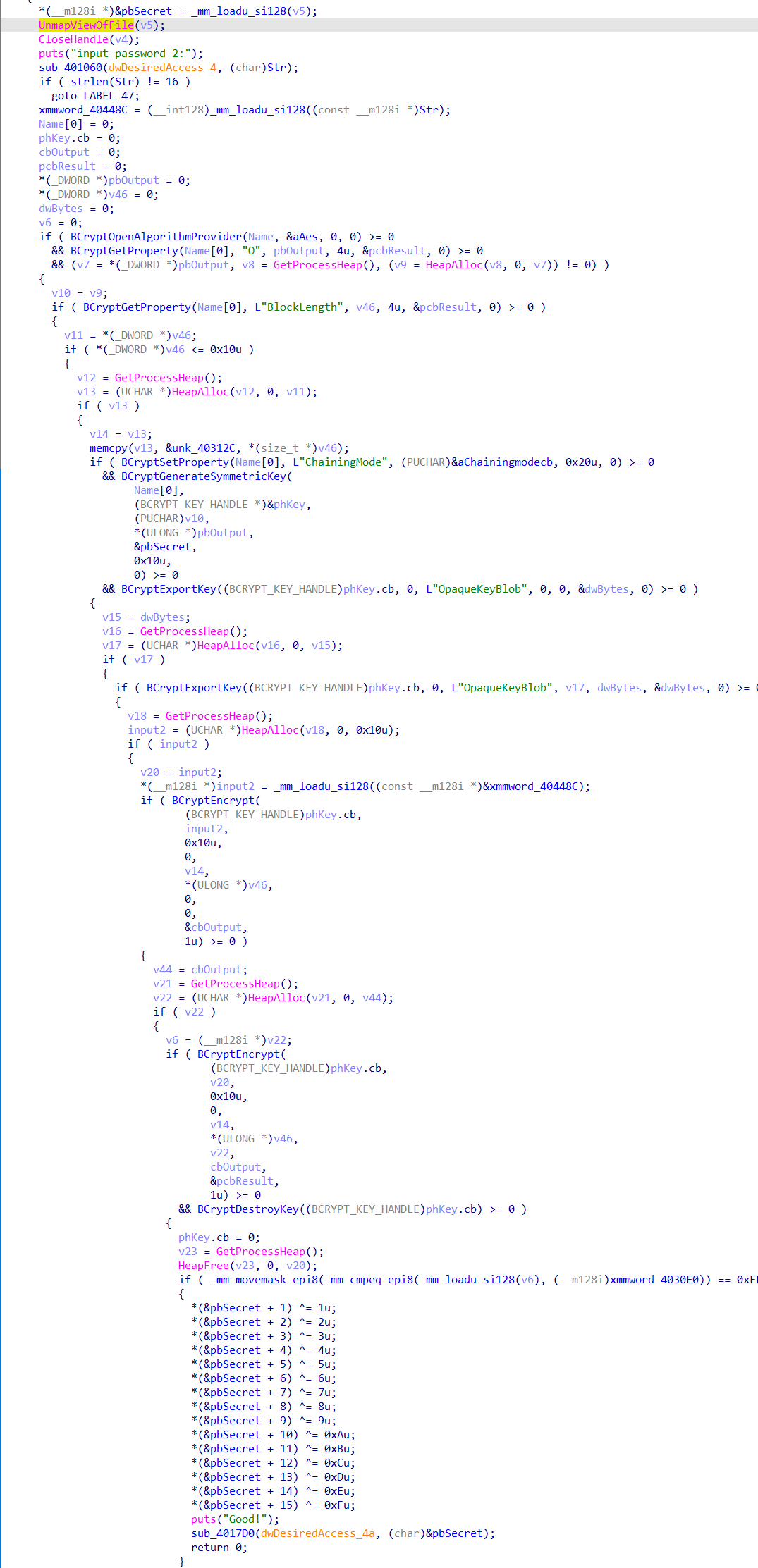
使用python解密一下得到pass2:
1 | #coding:utf-8 |
最后:hgame{2b0c5e6a3a20b189_7a4ad6c5671fb313}
fake_debugger beta
nc连上后,空格加回车进行单步调试。
容易发现,是对输入一位一位的异或加密后与指定值比较,不对则退出。
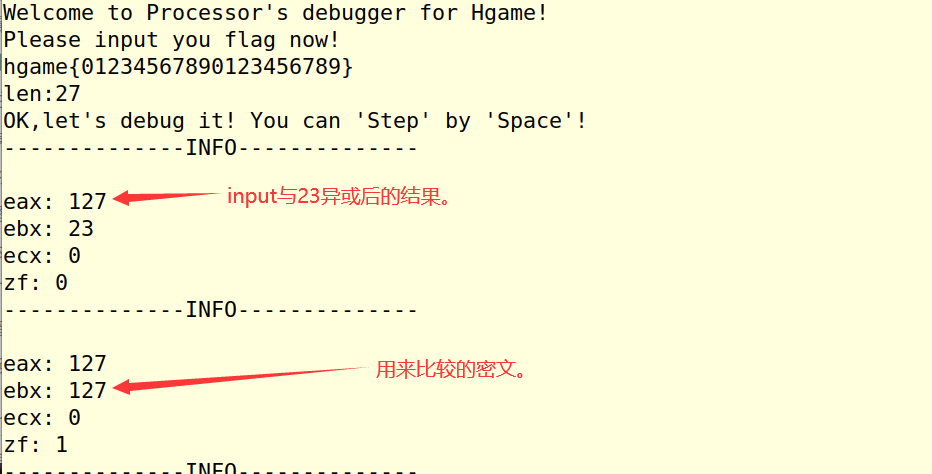
开始的格式是知道的,所以后面一位一位慢慢的跟一下就好了。
hgame{You_Kn0w_debuGg3r}
gun
jadx反编译后没有发现MainActivity,但从几个特征可以知道app进行梆梆加固免费版进行加固。
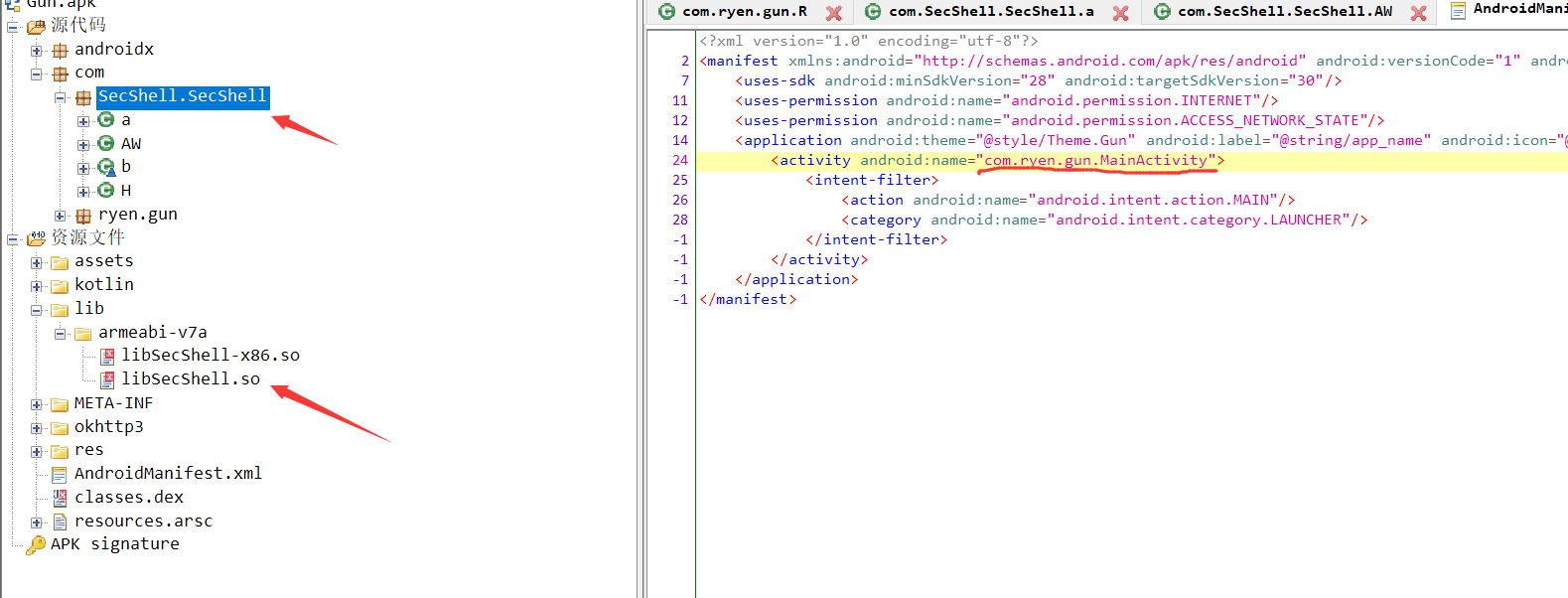
我们的目的主要是得到解密后的关键dex分析MainActivity,所以可以直接考虑用frida-dumpdex来dump出内存中的dex。项目地址:https://github.com/hluwa/FRIDA-DEXDump
搭建frida环境时注意一点:安装的frida的版本要和服务端安装的frida-server版本要一致。
dump出dex后从到小的拖进jeb中反编译,0xbf03a000.dex是我们要找的。
可以看到,创建了多个线程进行操作。
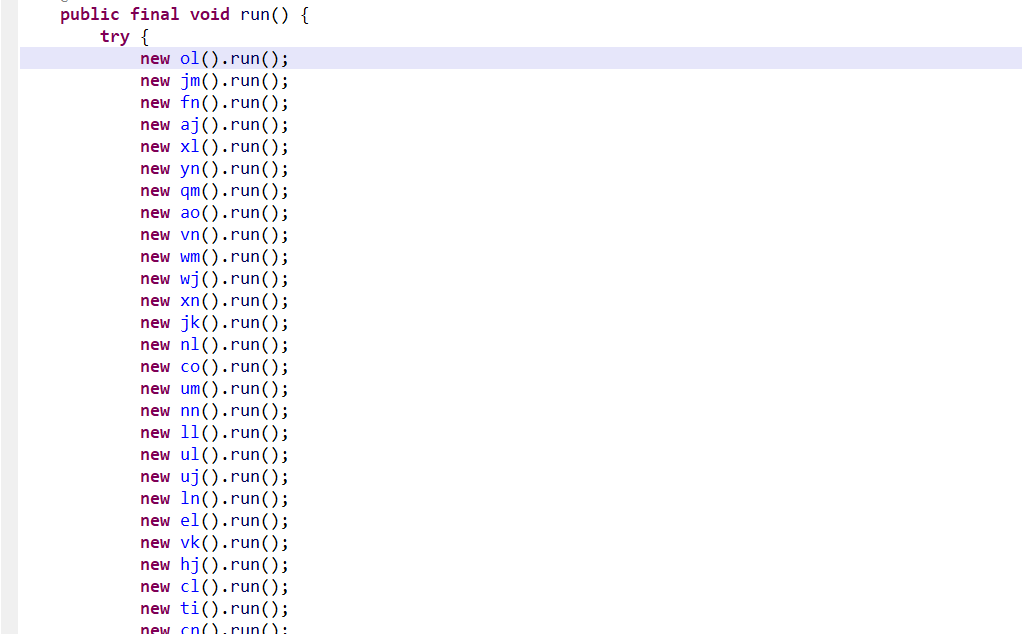
看一下功能:
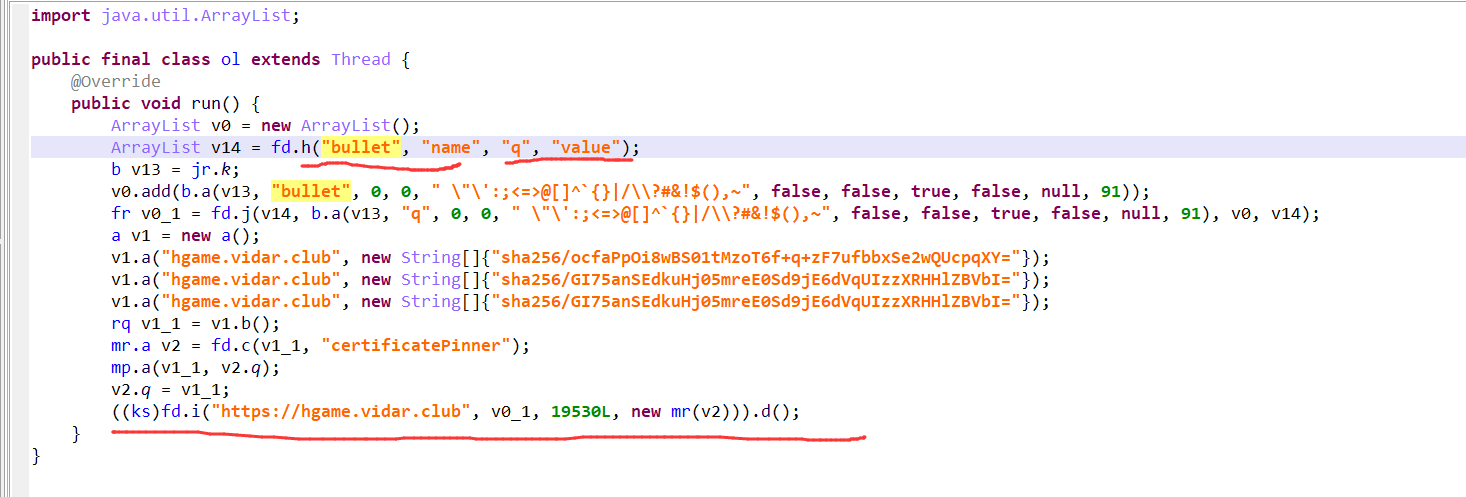
继续看fd.i方法:
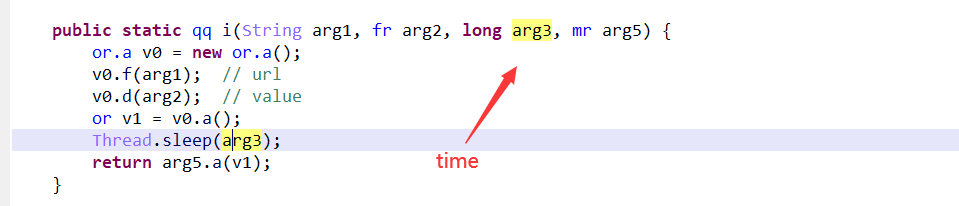
到这里基本上就可以知道,是开启多个线程进行发送数据,然后每个线程有不同的睡眠时间,这就有了先后顺序。
我是直接把所有数据按时间建立关系后,打印出来。
1 |
|
得到Oazsdgmpgmfuaz! ftq eqodqf ar ftq mbbe ue tqdq, ftue otmxxqzsq ue uzebudqp nk NkfqOFR arrxuzq omybmusz, ftq rxms ue tsmyq{dQh3x_y3_nk_z4F1h3_0d_zi7I0dw},可以看到最后和flag的格式是一样的了,字符数都是一样的,整个字符串的特征猜测凯撒加密。
从位移12得到结果:
FAKE
开始没注意,以为就是考下z3的使用,且题目中有提示:Try angr or z3.,上来就把36个方程组去写z3,没有发现解。。也可能是我的约束条件写错了。。
之后注意到题目名字fake,进而看了看程序,发现一个获取TracerPid的反调试和紧接着的smc:
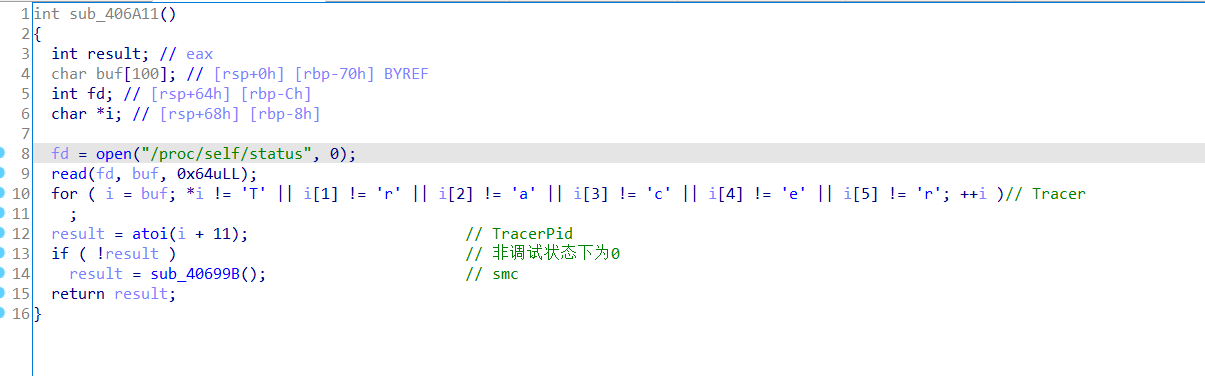
自己查看一下非调试运行时的状态:
使用idapython或调试到smc后的代码,其实就是2个矩阵的乘法:
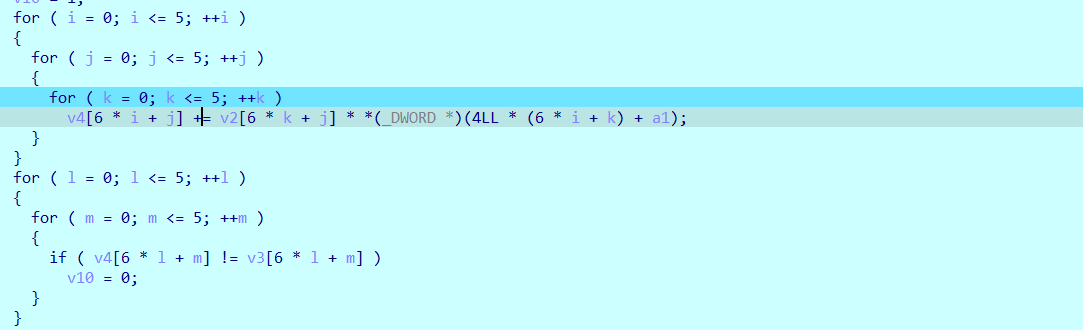
先z3解一下:
1 | from z3 import * |
再使用sage求解看,实质就是先求得一个逆矩阵然后与enc组成的矩阵做乘法。
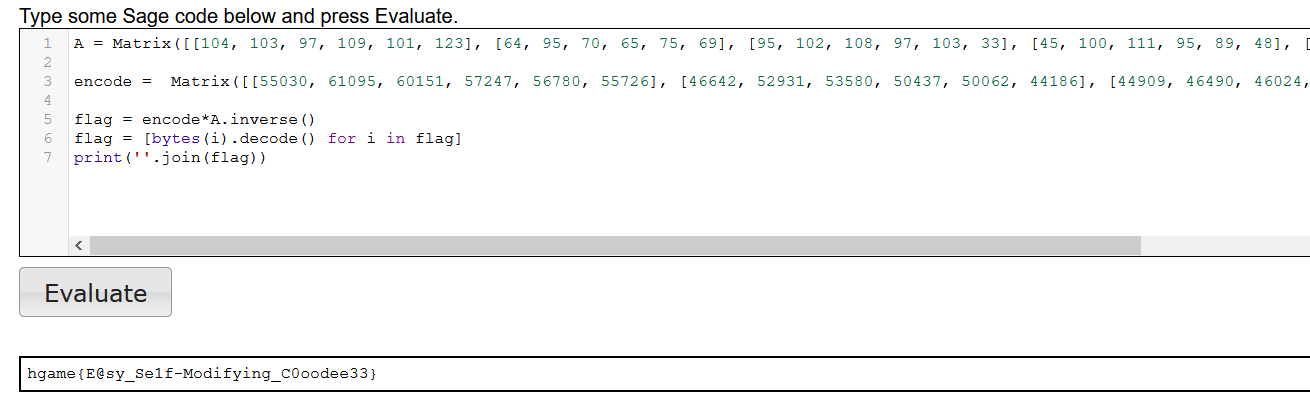
helloRe3
一血。
开始每管题目的提示信息,直接静态分析了下,看见创建了一个线程,后面开始注册窗口各种操作,然后越看越复杂,定位到这个函数,有iv,key和加密解密操作,从常量识别出是tea类的加密算法?但这个也无从下手,程序中好像没调用这里。。。
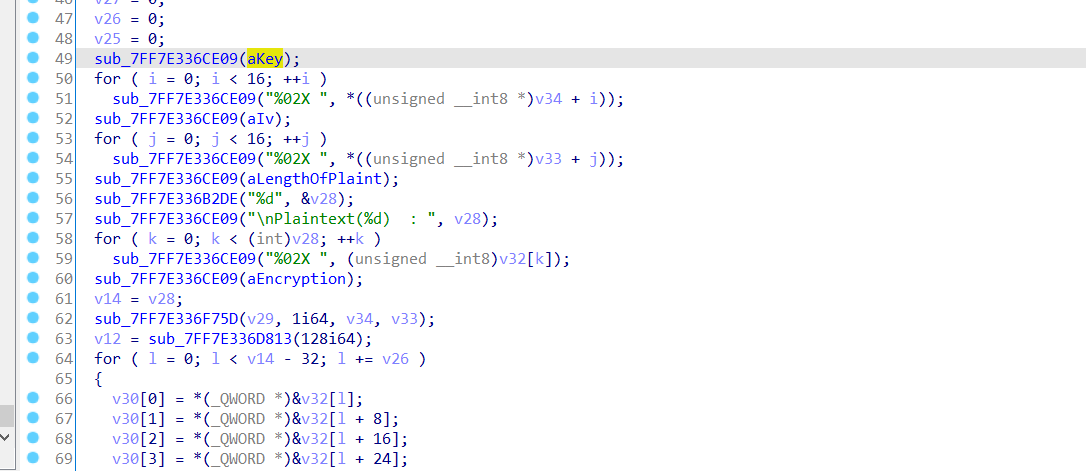
嗯,,回到题目开始看提示信息:开发者留下了调试信息,试试DbgView。就试试吧。
可以发现,每次输入都会输出相应的响应:
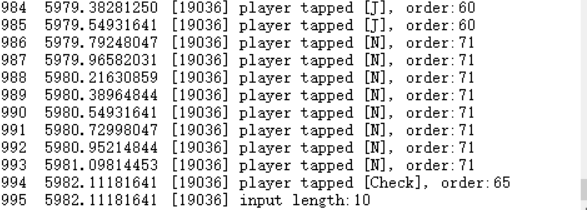
这里我直接去定位input length,因为之前静态分析时看见过。
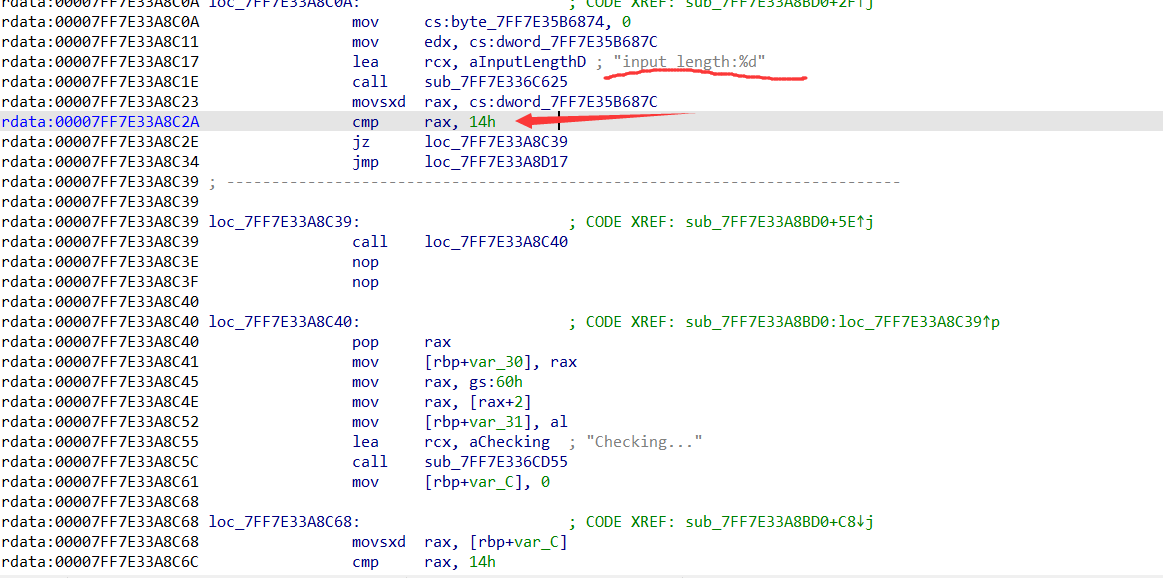
其实上面这个整个函数就是关键了,简单看下汇编,结合DbgView。
输入长度为20,每一位先和0xff进行异或运算,最后来个rc4加密再和密文比较。注意:输入的是每个字符的order值,从DbgView可以查看。
我直接附加调试得到内存信息,然后idapython得到order值:
1 | from ida_bytes import * |
最后用C语言写一个置表得到输入。
1 |
|
vm
二血。
一个简单的vm,调试跟踪得到先是找到输入的最后一位,开始从后向前进行指定值的异或运算,紧接着一轮从后向前的减法运算。
1 |
|
A 5 Second Challenge
一个扫雷游戏,第一步操作后,如果后面时间超过5s的话游戏结束。这个修改下系统时间就解除了。
找到关键数据文件夹:
反编译AFiveSecondChallenge.dll:看到获取当前系统的时间,检查是否超时的函数,题目描述的一样,对dll做了手脚,也是CheckBomAt这个函数,最后有很多数据,从数量可以猜测对应我们题目中的45*45的格子。
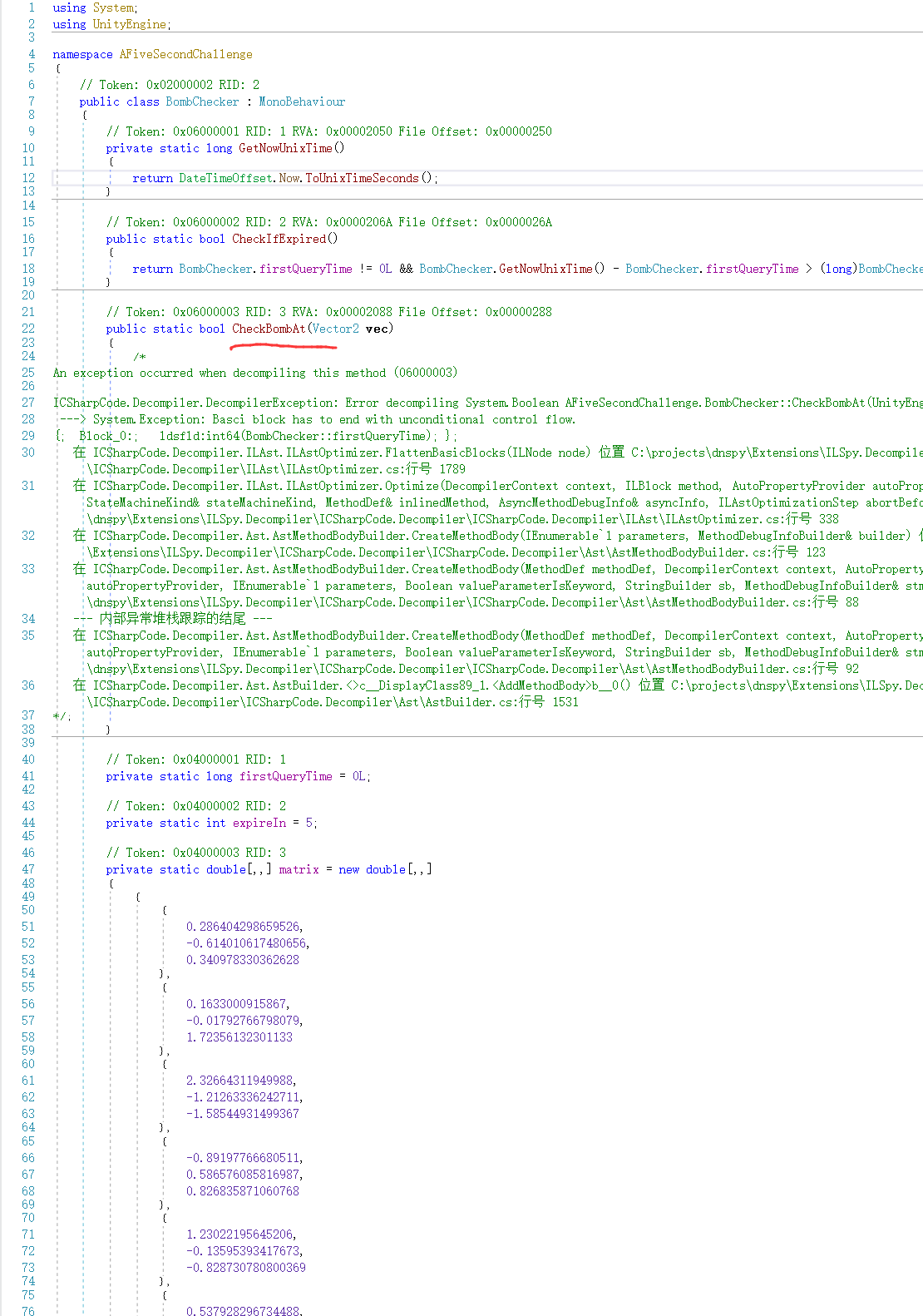
现在目的就是找CheckBomAt函数,开始想的是可能有办法修复这个dll,搜索一番没有结果。
转到刚刚那个文件夹的,发现2个关键cpp文件:AFiveSecondChallenge.cpp,Assembly-CSharp.cpp。
在AFiveSecondChallenge.cpp中发现反编译不出来的函数:从名字可以很好识别其功能,开始做一个超时检查,如果没超时取出matrix中的数据做一个运算后判断。
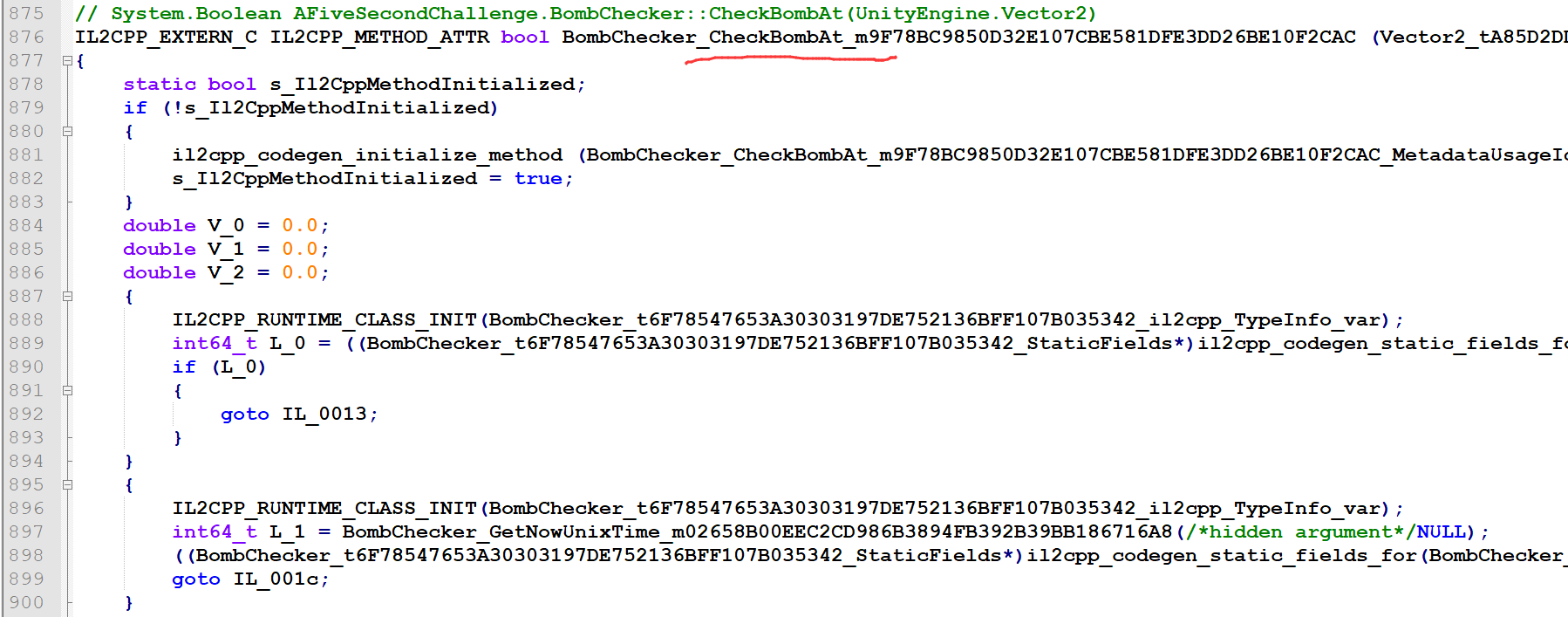
然后从Assembly-CSharp.cpp中看到了整个游戏逻辑。注释相当于把源码都给了吧,真好。
捕捉鼠标点击后,开始进行各种判断。
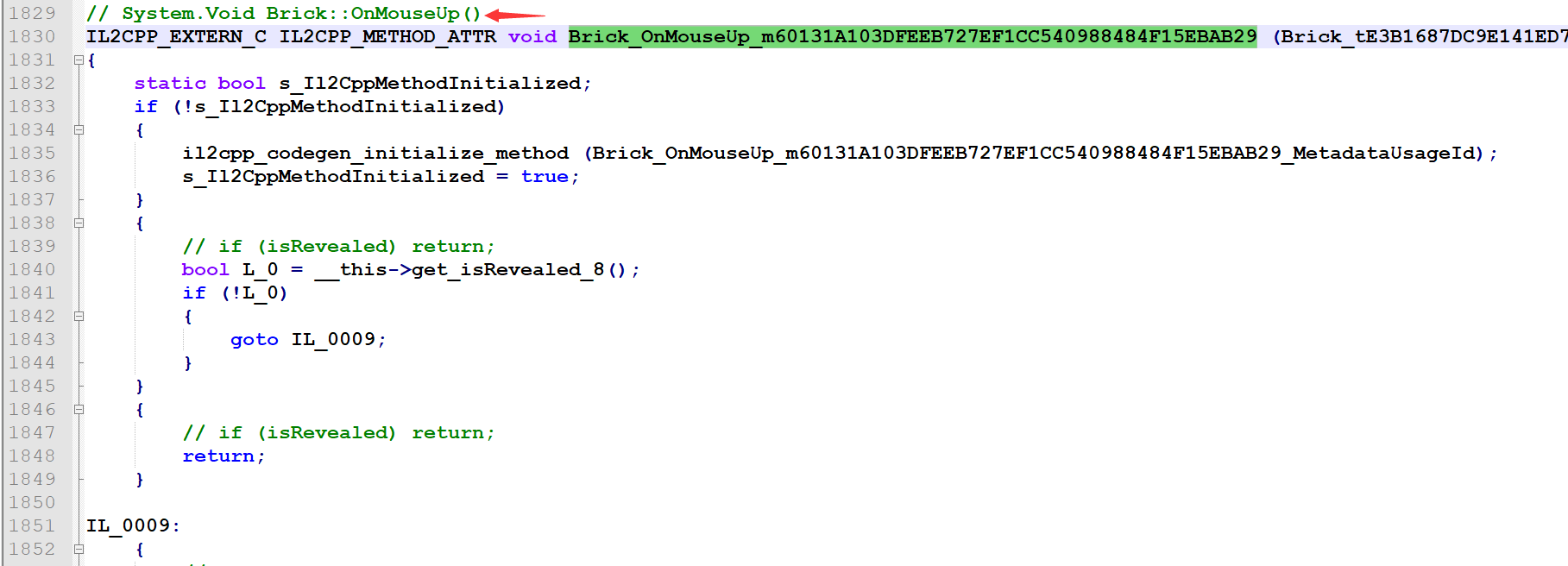
计算周围的雷数,就是判断8个方向,也可以看出返回值为0代表不是雷:
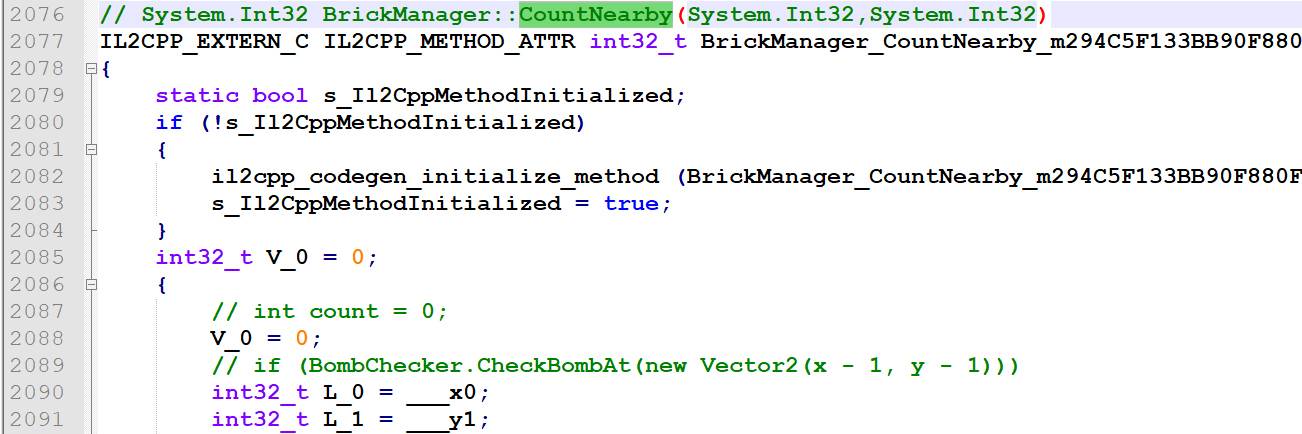
点击后,根据是雷或者不是雷填充对应的色块:
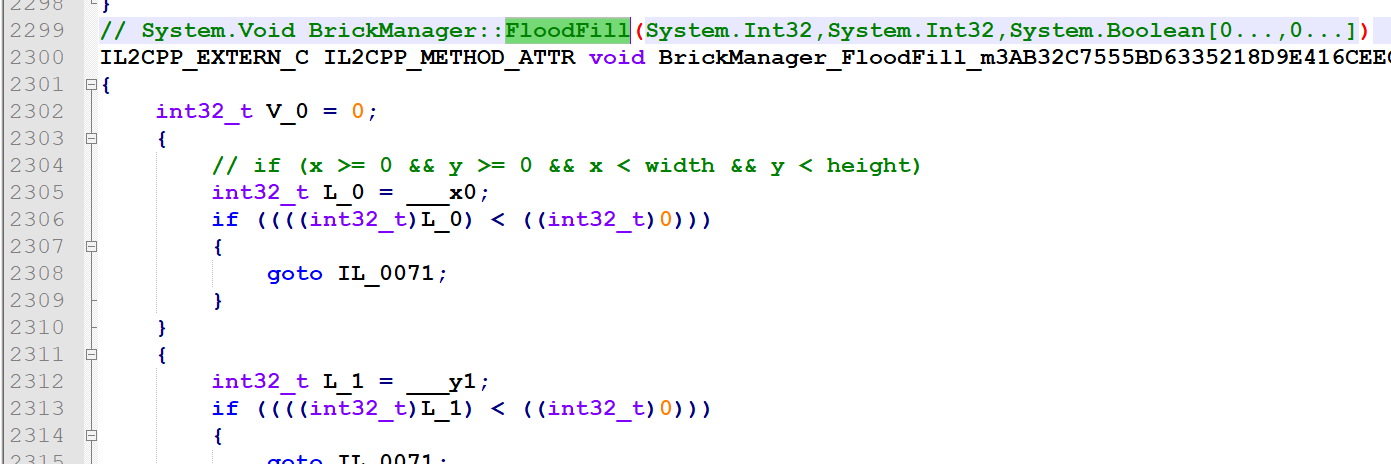
如果点击块周围没有雷,则递归的向四个方向扩展开来:
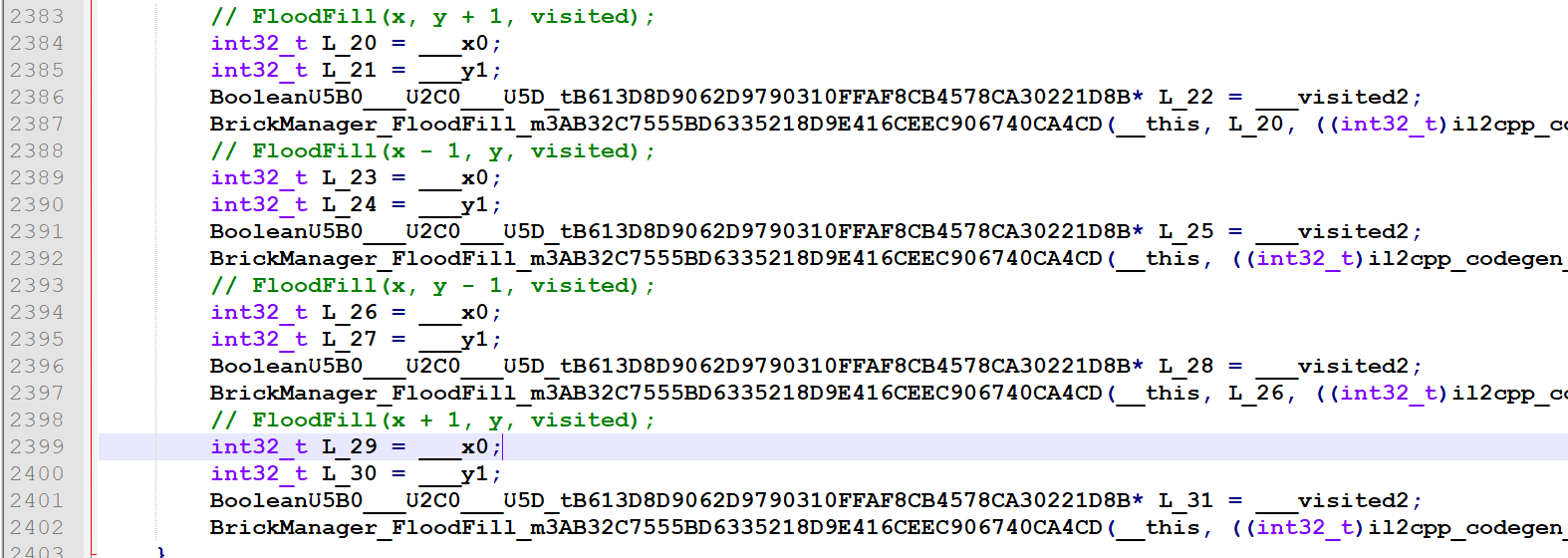
分析到这里想找最后胜利的判断条件以此看flag怎么来的,好像没有,。。
到这里知道了关键就是判断一个块是否是雷的函数CheckBomAt,按照题目的算法打印出雷的位置,1表示雷。
1 |
|
用这个数据玩了一下游戏,但是有的地方和算出的雷的位置不一致,大多数还是一样的。。然后一直找是不是哪里算错了,算法也比对了好几次。。就把题放一边了。
后面看见题目给出提示,二维码,看了看我之前打印的数据。。。
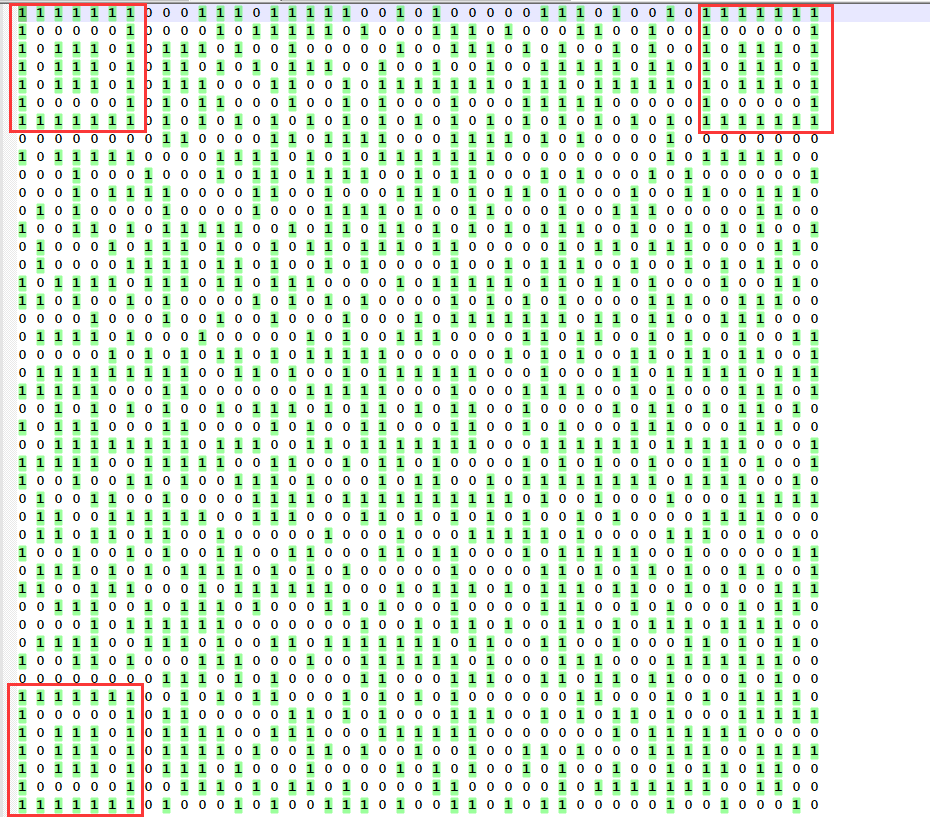
使用python的PIL模块用这个数据打印出二维码:
1 | from PIL import Image |
扫一下得到flag:hgame{YOUhEn-duO_yOU-X|DOU-sHiun1Tyk4i-fA_de_O}
nllvm
一血。
通过这个题学习熟悉下AES加密算法还是不错的。
首先看一下main函数:先设置控制台显示文本的属性,接着可以看到很多异或运算,这些数据在要使用后同样做了相同的异或运算,所以简单隐藏了下程序中的数据。
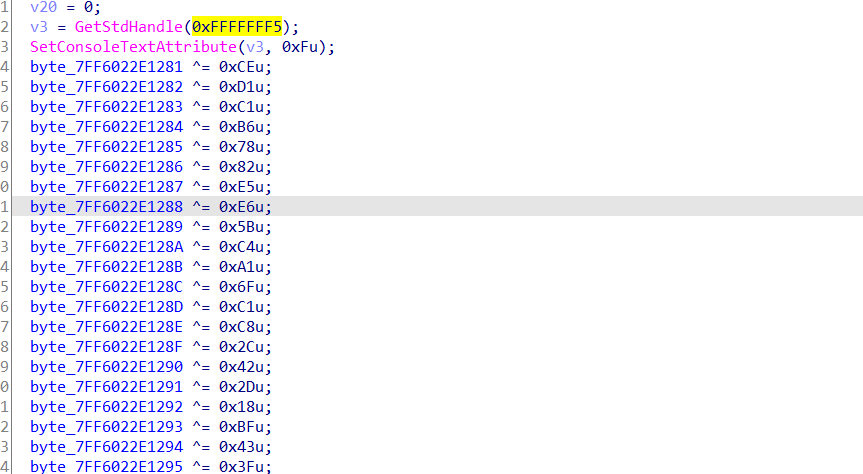
找到加密的地方,开始静态看了一下整个加密流程,只是注意到很多异或运算也不复杂,在一个置位的地方发现加密后的一个aes的s-box。
确定aes加密后,又进而发现是带有iv的。
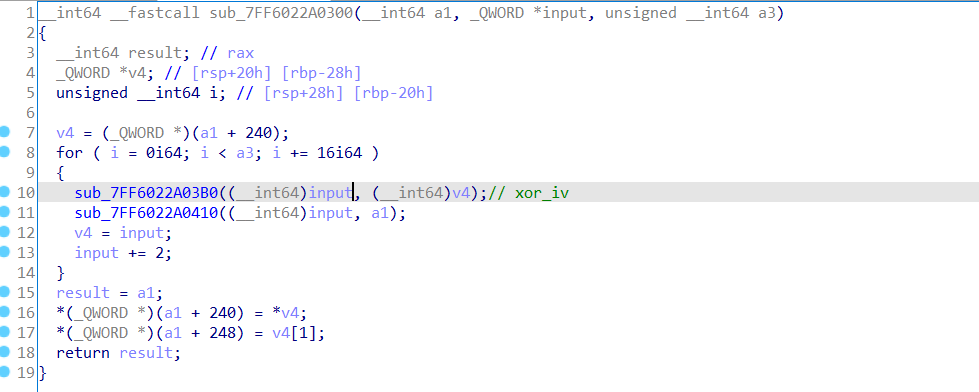
再梳理了一下这里的加密流程:
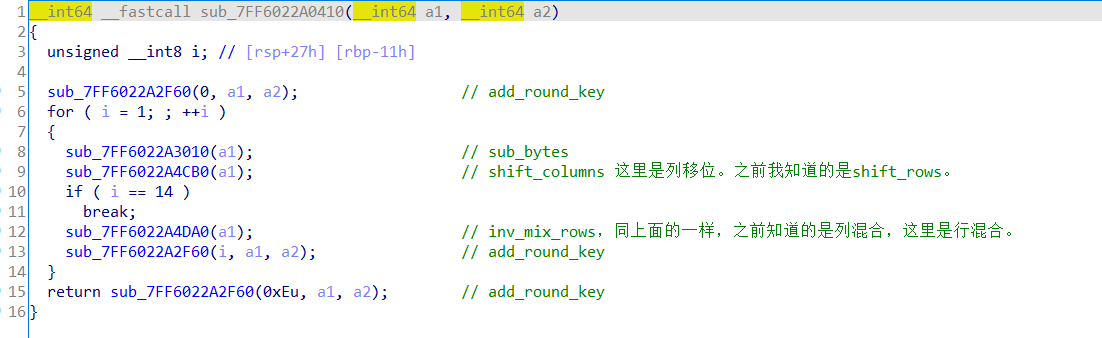
可以从重复轮进行了13次可以知道key是256位的,但块长度是128位的。。之前一直以为密钥长度和块长度是一样的。又加上这里移位和混合的方向和我之前了解的正好相反,就感觉是魔改过的aes加密,开始用C自己写逆过程,关键就是行混合不好写,还好有搜索,hh。
1 |
|
其实写好逆过程后,开始一直解不来,后面一个一个排查再发现是密文找错了,再次被从ida的伪代码来看变量的值坑到。。。
另外这个aes加密并没有魔改的,后面我又用python的aes模块解了一下,同样解出。。那现在问题就是移位和混合的方向的问题(这里先留一下),后面再好好学习一下。至于块长度和密钥长度是没关系的。
最后就总结一下aes加密的大概:
- 重复轮:128位密钥一般重复执行9次,192位密钥一般重复执行11次,256位密钥一般重复执行13次。
- 重复轮每轮重复的操作包括:字节替换、行移位、列混乱、轮密钥加。
- 在aes中块长度与都是128位,与密钥长度无关。
- 每执行一块的加密操作,开始是一个初始轮(与初始密钥异或),然后重复轮,最后一个最终轮(除开列混混合操作)。
Misc
Base全家福
从每一步骤后的字符组成可以容易辨认出来。
base64,base32,base16
不起眼压缩包的养成的方法
从图片最后看到一个压缩包和提示密码是图片id。
https://saucenao.com/ 上这个网站查该图片的id。
解压后得到plain.zip和NO PASSWORD.txt,而plain.zip又要密码,看了一下里面的文件,发现也有一个NO PASSWORD.txt文件,它们crc32值。
这由此想到应该是明文攻击了,而明文攻击有一个条件,2个文件的压缩方式要相同,这在NO PASSWORD.txt中有提示。
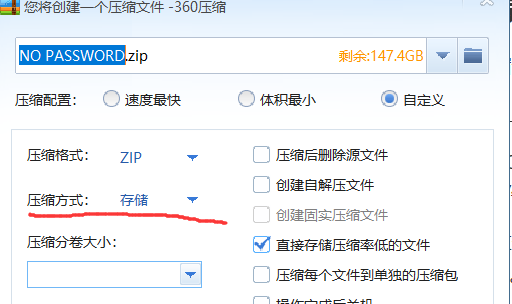
明文攻击得到密码:
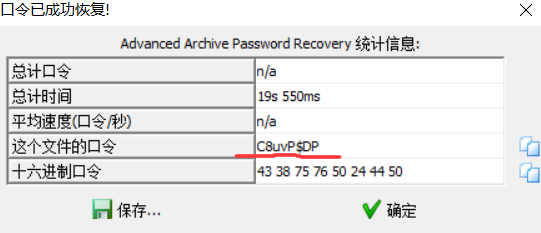
最后打开flag文件,是实体编码 entity code,用html写处一个标题让浏览器解析它。
1 | <h1>hgame{2IP_is_Usefu1_and_Me9umi_i5_W0r1d}</h1> |
