Reverse:
WannaFlag
打开程序,炫酷的界面和音乐。其实就是一个CrackeMe。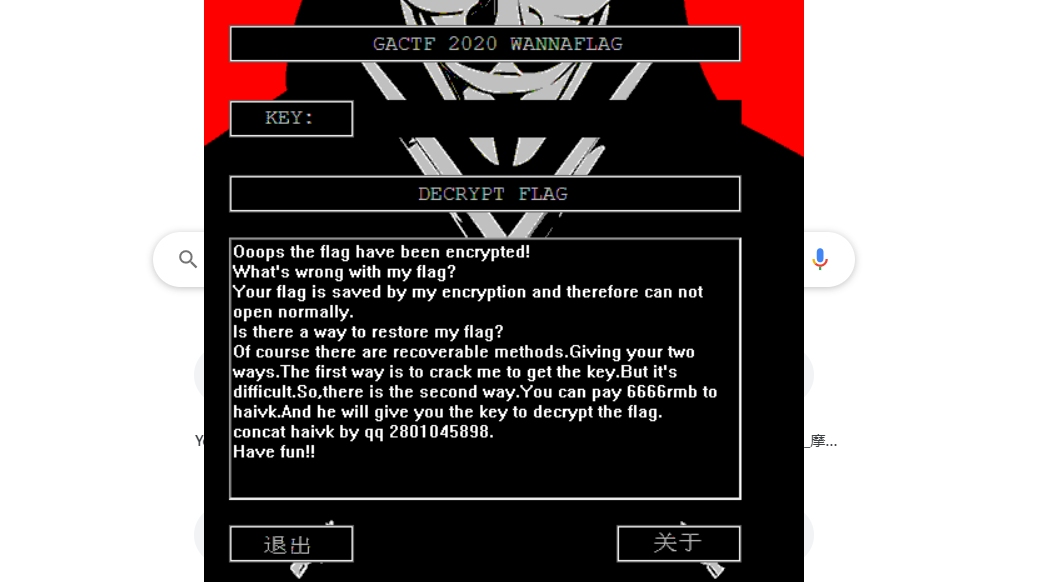
载入ida,直接定位到GetwindowText或者GetDlgItemText函数。

关键就是那个复杂的if语句根本就执行不到,直接跳过。
对input进行了xor与ror操作。直接逆即可:
1 |
|
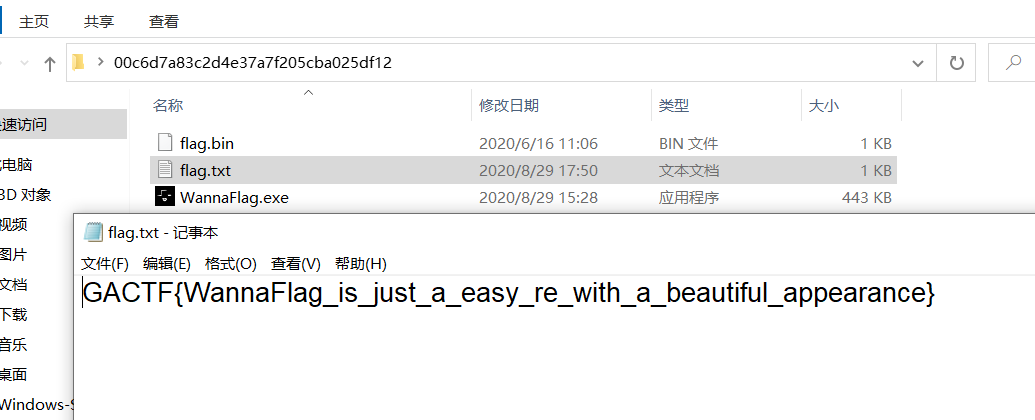
最后将其输入程序的输入框,打开解密后的flag文件得到flag。
EasyRe
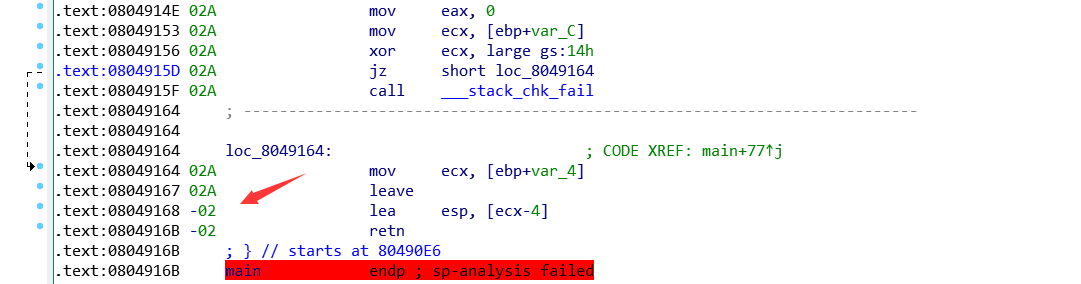
ida打开后,main函数sp-analysis failed,简单修复一下栈指针就行。
来到main函数,首先是输入一个整型数据,从交叉引用发现对该数据后面并没有使用,猜测对函数代码有一个解密过程。发现后面有一个mprotect()函数修改指定内存保护属性,即把要解密的代码的内存改为可写。接着的函数实现解密一个函数代码功能。
动调来到解密的函数(这里我也反复修了几次,才完美的F5):一个VM且前面已经申请了存放数据的内存空间和初始化。
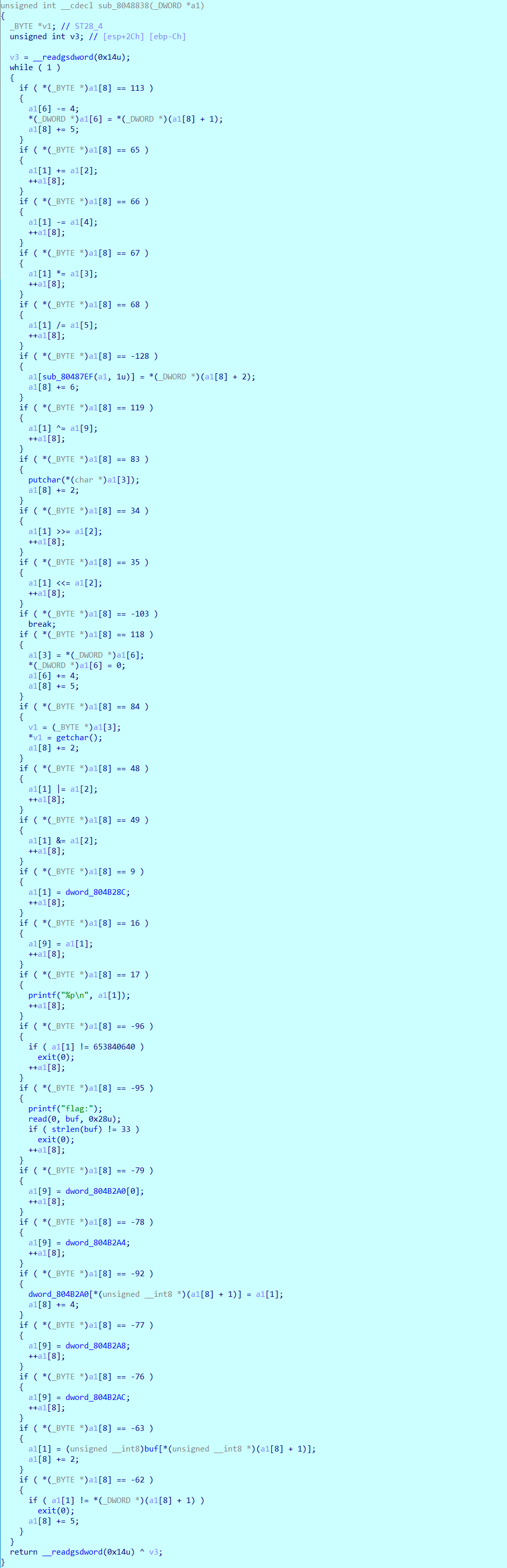
开始是单步调试,由于分支比较多,后面将整个函数与opcode复制到C语言编译器,打印出函数根据opcode的执行情况:
1 | a1[1] = input |
从上面打印出的执行,整个程序就很清楚了。
首先就是逆出输入的第一个整型数据,但看了下算法,确实麻烦。。正好之前学习了下angr符号执行,用这个题尝试一下。
1 | import angr, claripy, sys |
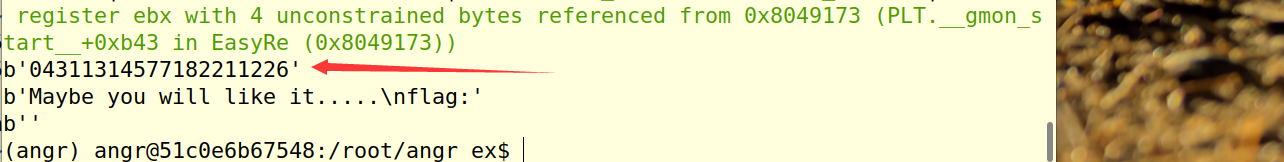
很快得到了答案,尝试输入一下,正确。
开始使用这个整型数据计算出dword_804B2A0数组中的4个值。
刚刚计算完准备依次逆出flag中的每一位时就想到,其实可以不用计算第一个输入的整型数据,因为给了flag的格式为GACTF。。。根据这个就可以计算出dword_804B2A0数组中的每一位。。
开始利用之前复制到C语言编译器中的代码打印出flag中每一位与dword_804B2A0[]数组异或的是哪一位,与最后需要用来比较的数据。
最后算一下,得到flag:
1 |
|
其实也是很简单的一个题,利用flag的格式。。
Misc
SignIN
将二维码拼接一下,扫出flag。

welc0me_t0_GACTF_have_Fun
crymisc
一个word文档,但是打不开。拖进010editor查看,发现504B(PK),是一个压缩包。
改文件后缀后其中一个文件解压失败。
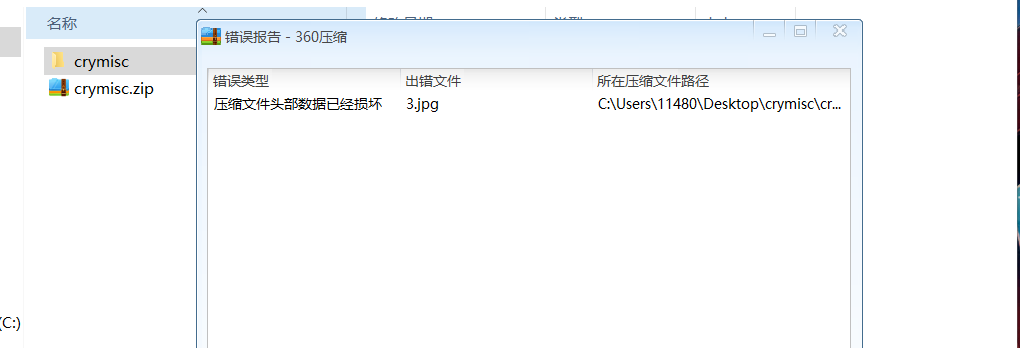
谷歌看见可以使用winrar来修复一下。
下载后,在winrar中打开却是提示有密码。。那就猜测是伪加密了。。下面修改为偶数即可。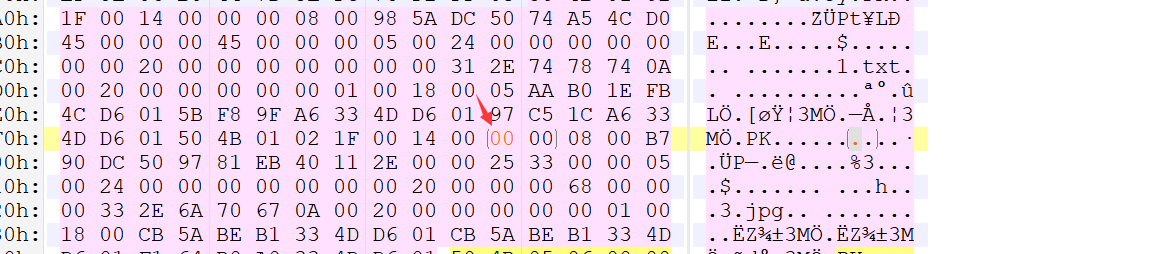
360压缩还是奇妙,伪加密文件直接提示文件出错。。
然后打开一张图片和一个文本文件。文本文件没有什么,查看图片二进制信息。在最后发现: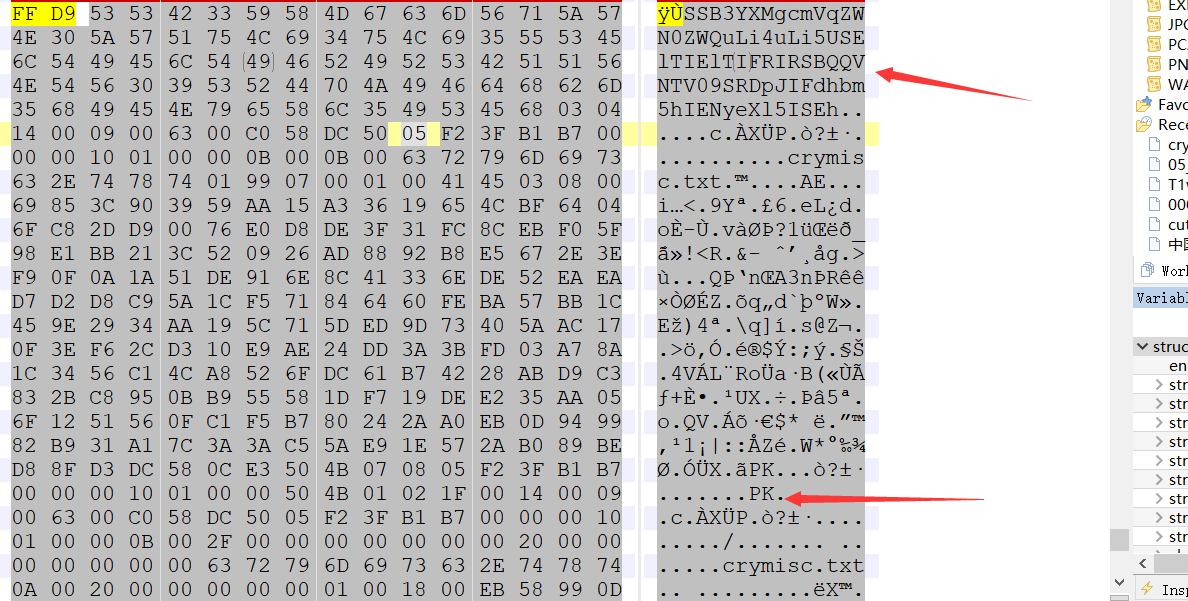
又是一个压缩包,但在开头出现一个字符串,从组成猜测是base64加密。解密得到: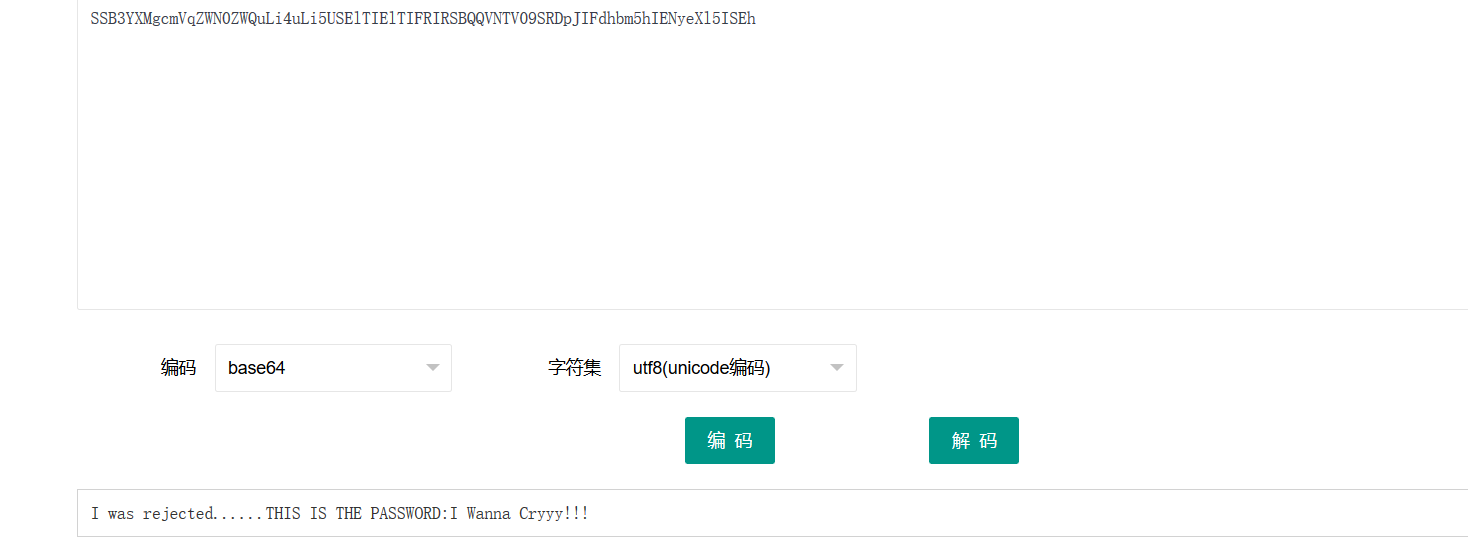
看来是后面压缩包的密码。然后把该压缩包的头补全(504b),输入密码解压: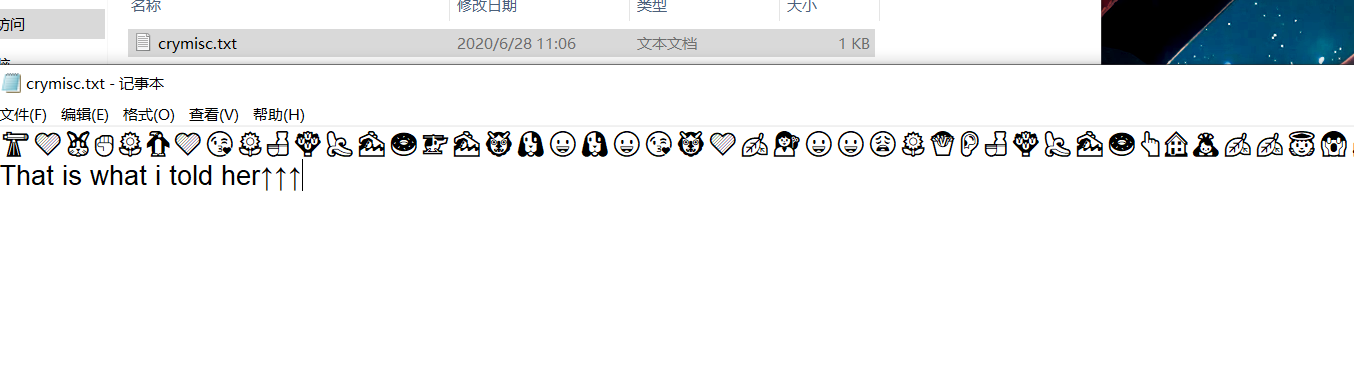
到这一步就一直卡住了。。。实在没见过这个表情密码,谷歌百度查到的信息又不会用,,,
比赛完了才从一位师傅哪里知道要自己从github找到这个项目自己搭建一下环境,然后根据一张表映射关系解密。。。
根据师傅的指导搭建完后,从题目也很容易想到解密的key是哭脸表情。
最后解密: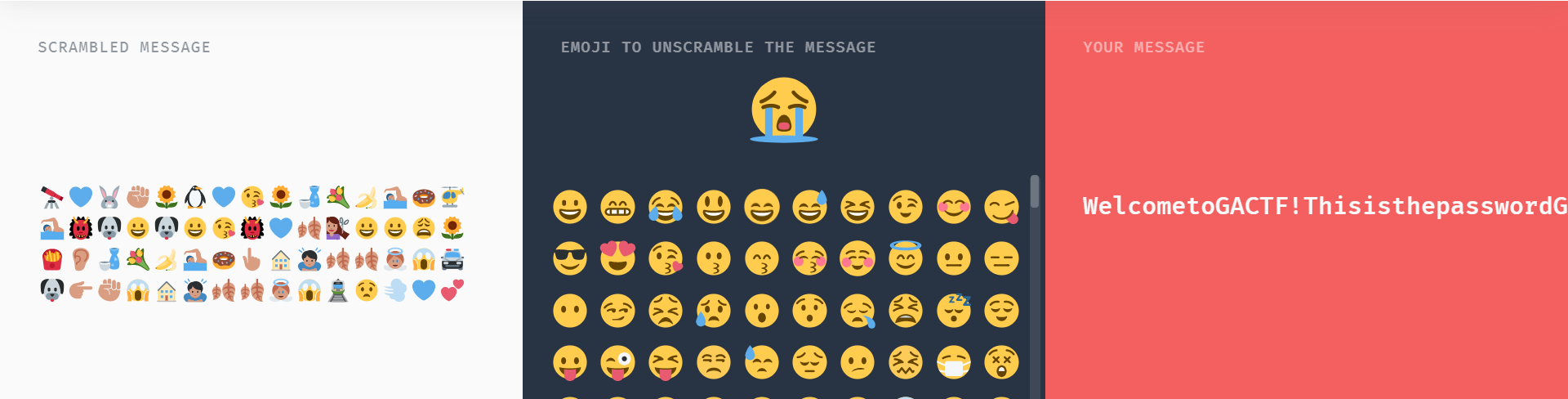
还有一个坑就是,下面的表情其实是同一个,我还纠结半天。。