Reverse
T0p Gear
64位elf文件加了upx壳,脱壳后载入ida中发现伪代码不好看,就直接看汇编。就三个检查函数。
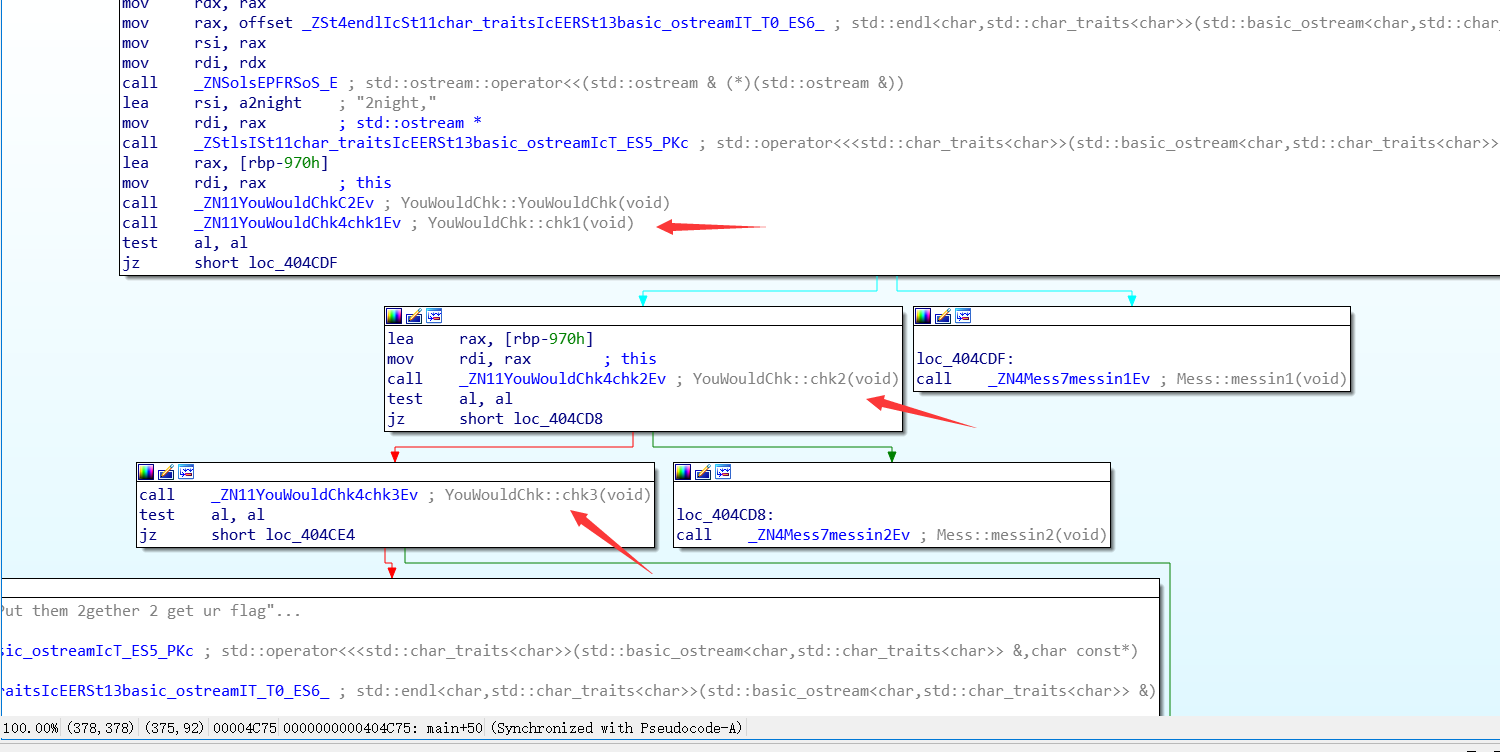
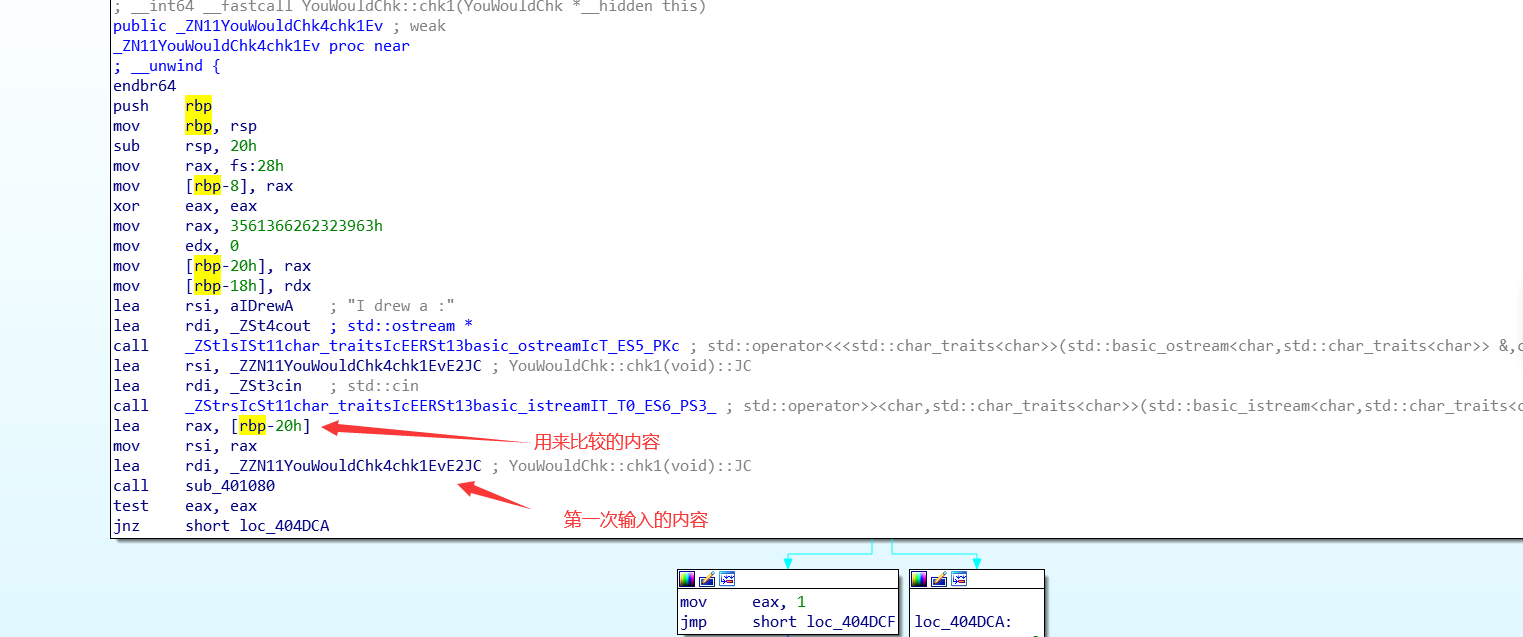
chk1:可以看到,只要知道栈中rbp-20h的内容即可。这里直接看或者动调都简单。
chk2:与ch1同理。
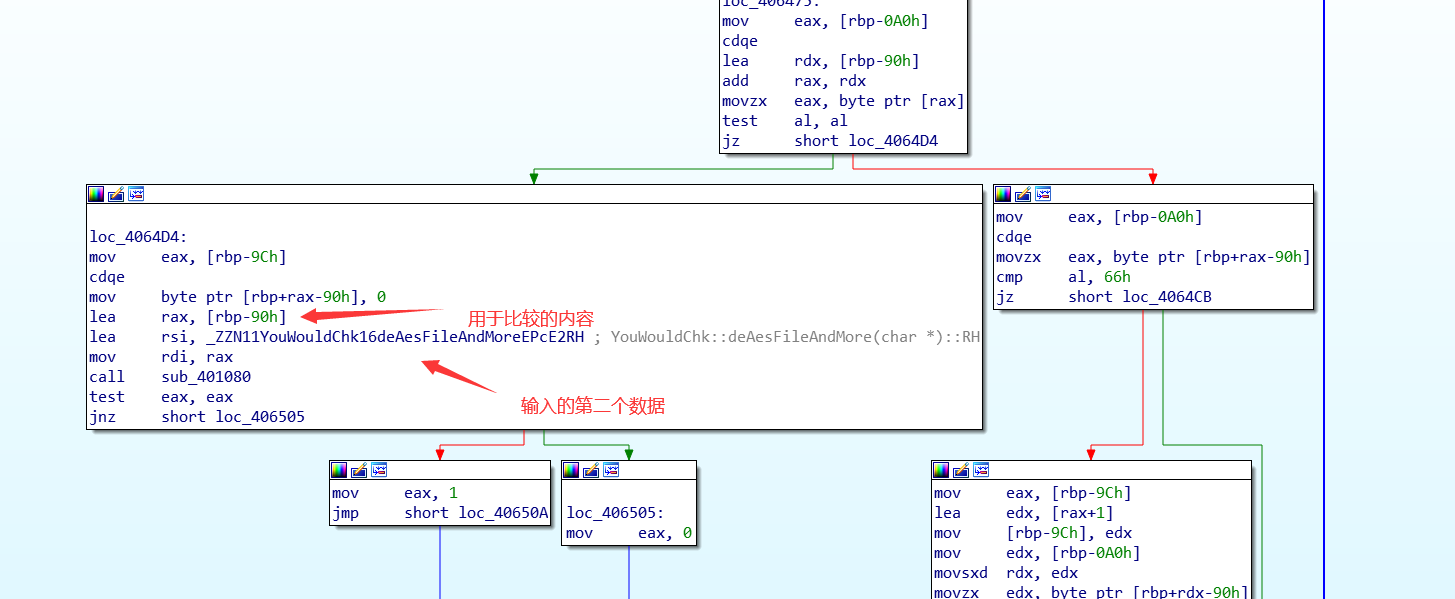
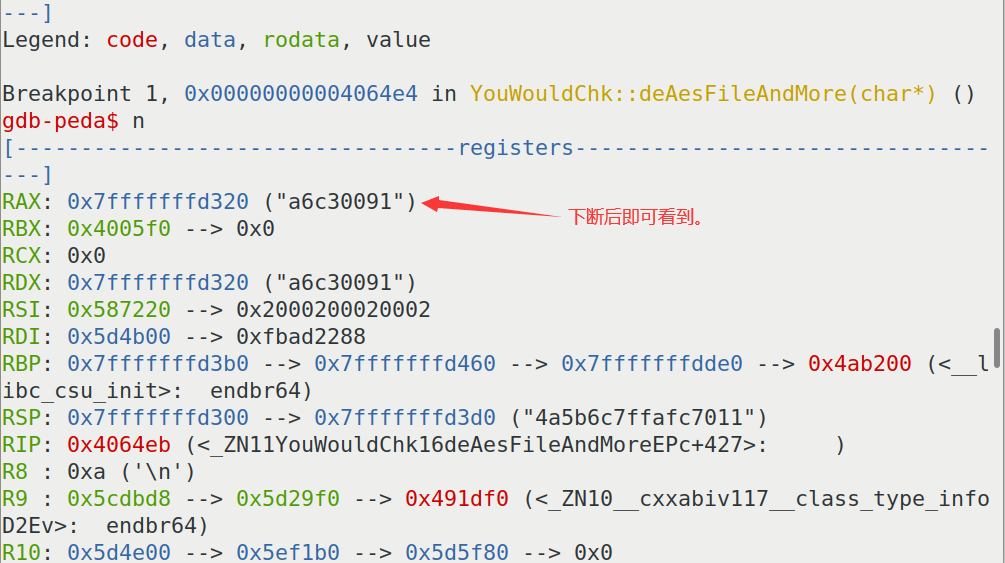
chk3:与上同理。
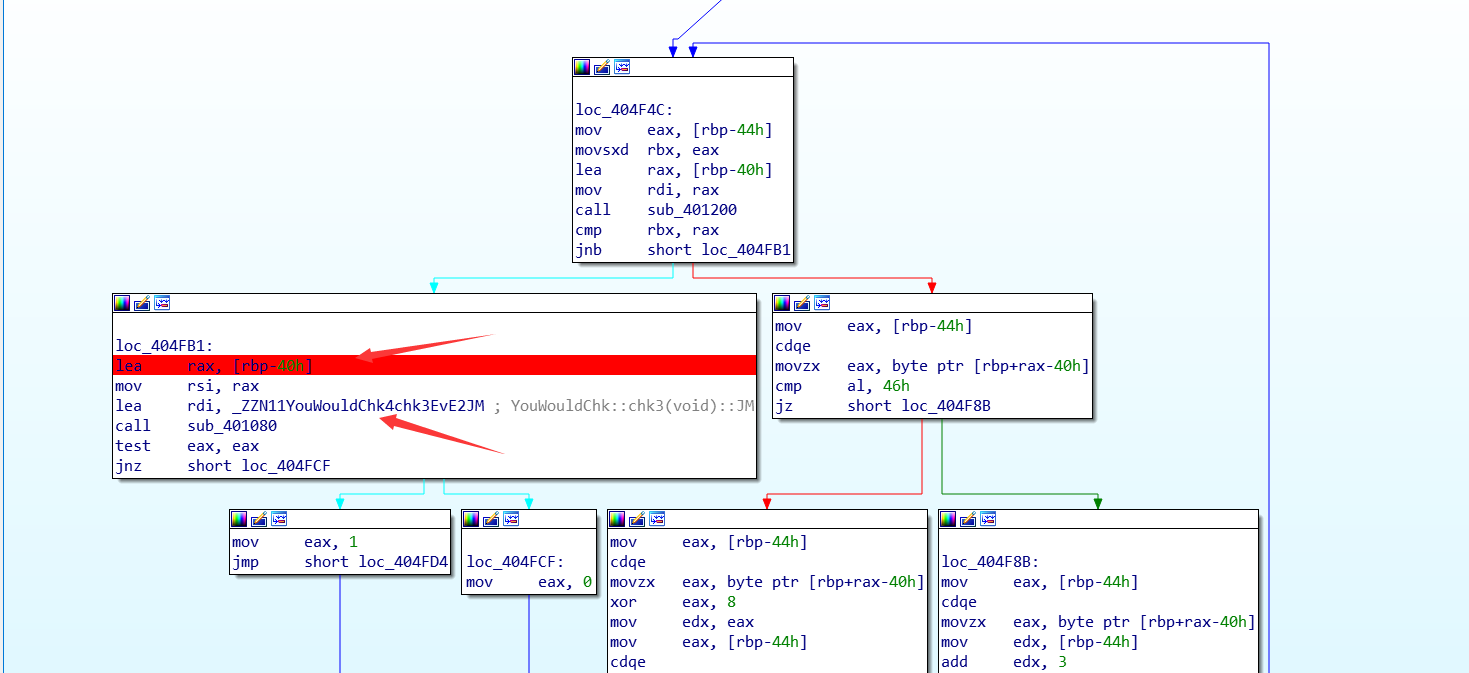
最后将得到的数据结合起来即可:c92bb6a5a6c3009124566d882d4bc7ee
easy_maze
64位elf文件,载入ida中看一下,知道是迷宫题,所以目标是明确的。
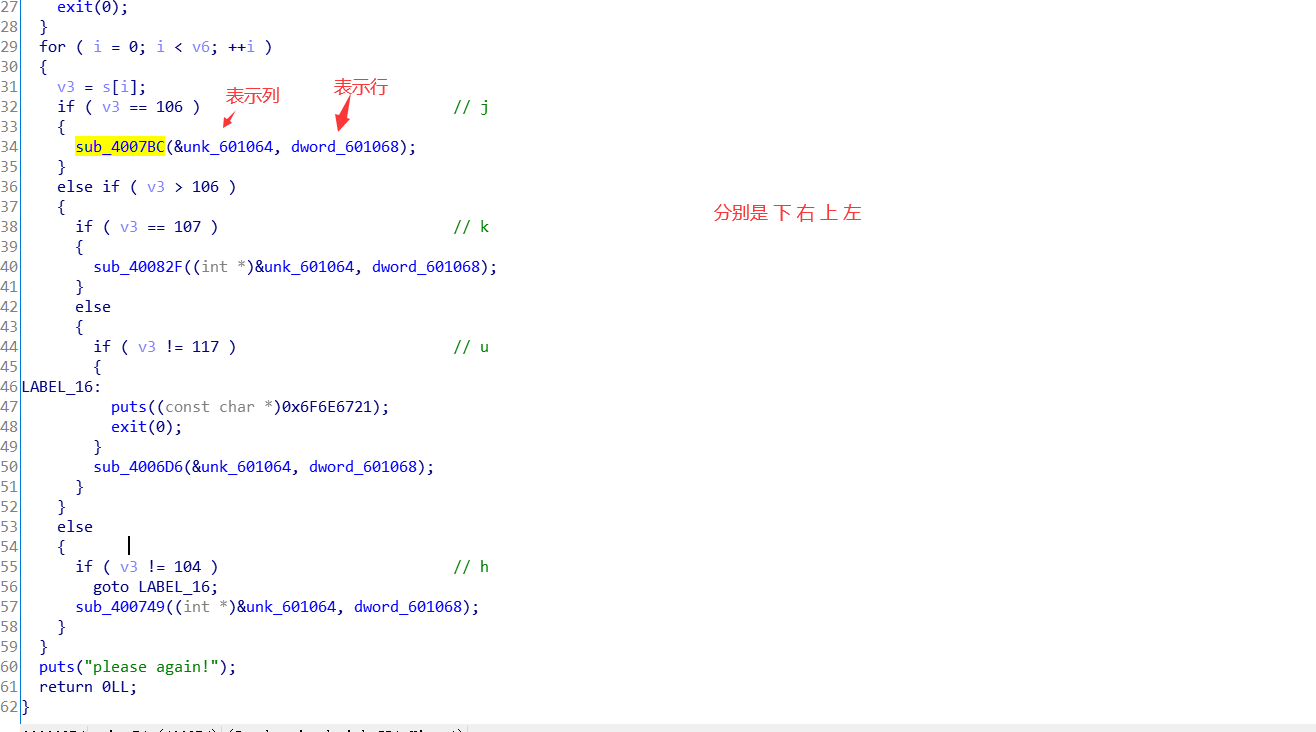
可以知道刚开始列和行都是0,下面找迷宫图。先随便看一个操作函数。
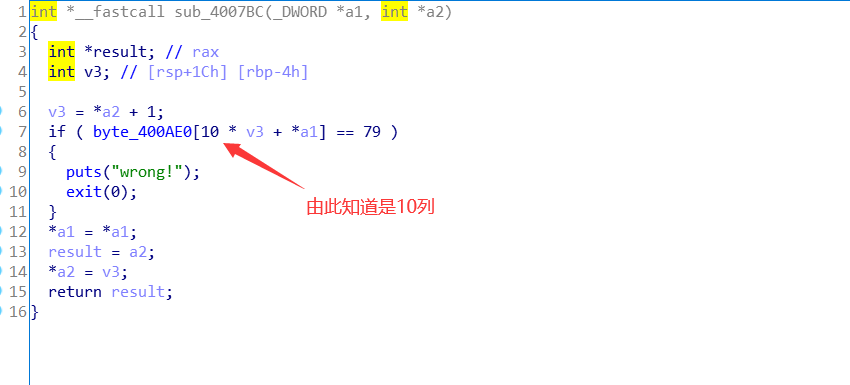
查看byte_400AE0:把数据提取出来。
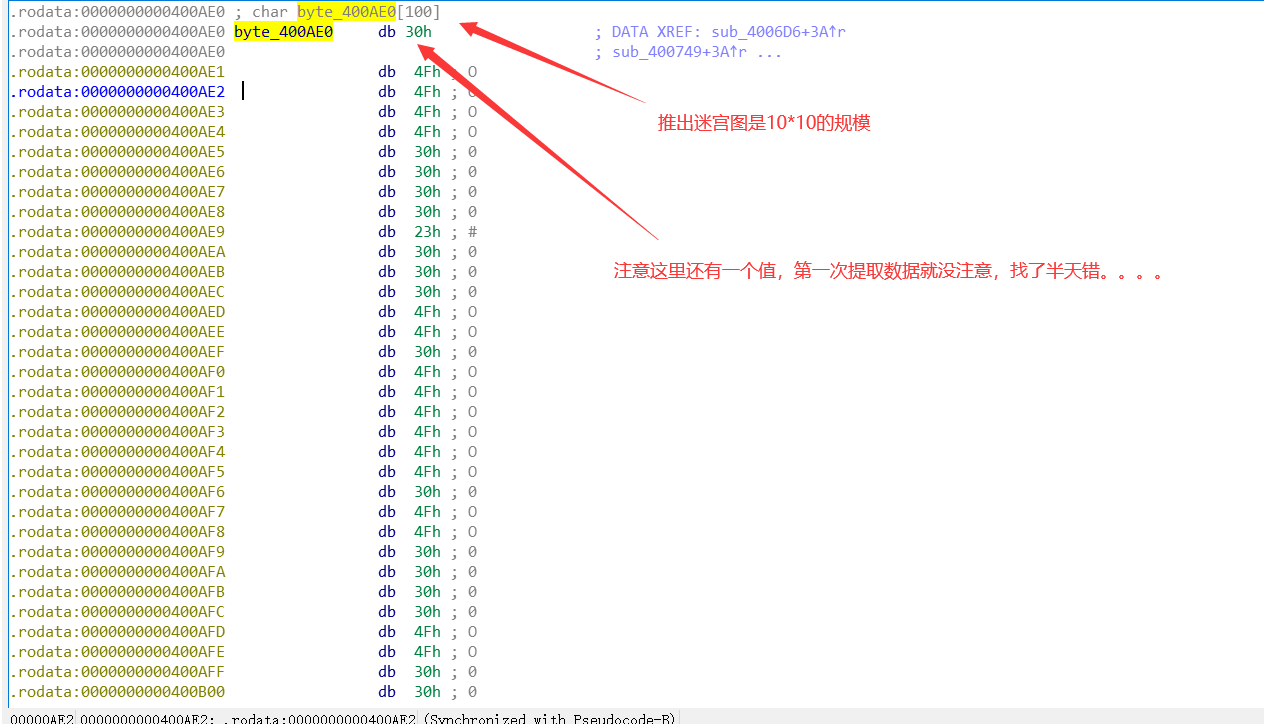
用C语言将图打印出来。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
int main(void)
{
int i = 0, j = 0;
char ida_chars[] =
{
49, 79, 79, 79, 79, 49, 49, 49, 49, 35,
49, 49, 49, 79, 79, 49, 79, 79, 79, 79,
79, 79, 49, 79, 79, 49, 49, 49, 49, 79,
79, 49, 49, 79, 79, 79, 79, 79, 49, 79,
79, 49, 79, 79, 79, 79, 49, 49, 49, 79,
79, 49, 49, 79, 79, 49, 49, 79, 79, 79,
79, 79, 49, 79, 79, 49, 79, 79, 79, 79,
79, 79, 49, 49, 49, 49, 79, 79, 79, 79,
79, 79, 79, 79, 79, 79, 79, 79, 79, 79,
79, 79, 79, 79, 79, 79, 79, 79, 79, 79
};
for(i = 0; i < 10; i++)
{
for(j = 0; j < 10; j++)
printf("%c ", ida_chars[10*i+j]);
putchar(10);
}
return 0;
}
由于0和O不易区别,自己把0换成了1。最后从1绕过O走到#即可。jkkjjhjjkjjkkkuukukkuuhhhuukkkk 再mad5加密一下。
Magia
没看见题目的提示,在找密码的时候所有情况试的。。。
32位PE文件,首先打开看了下, 提示输入一个密码,然后验证。ida中看看。
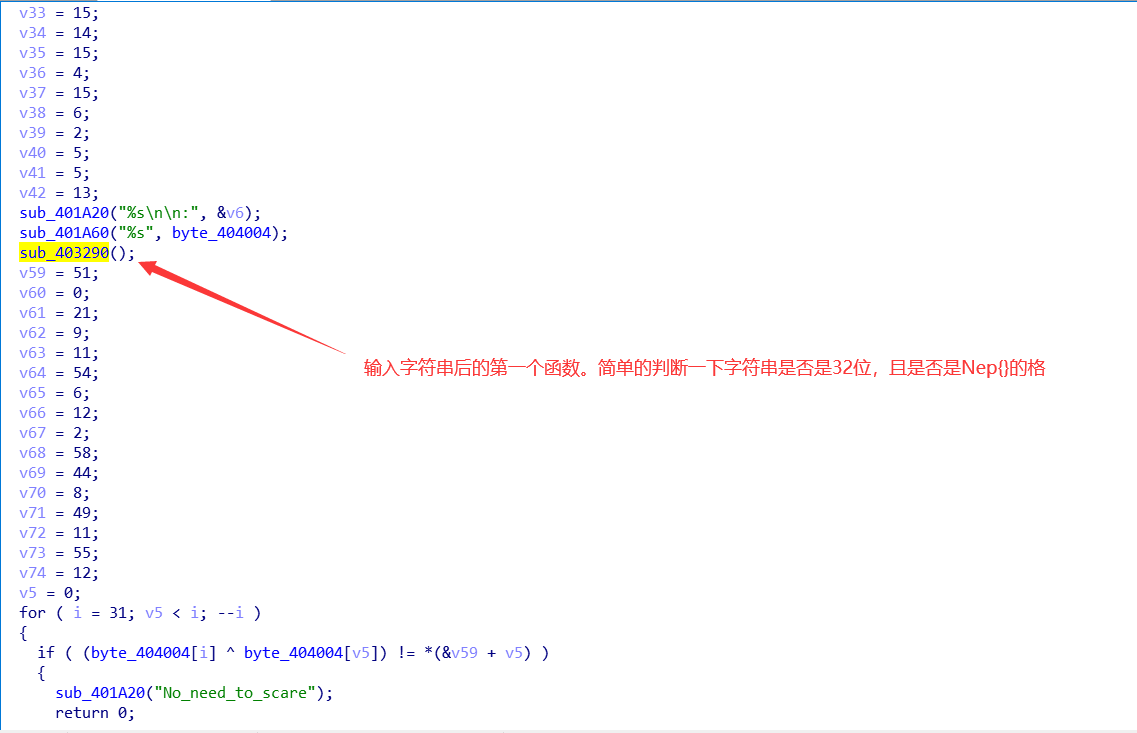
接着看下面:
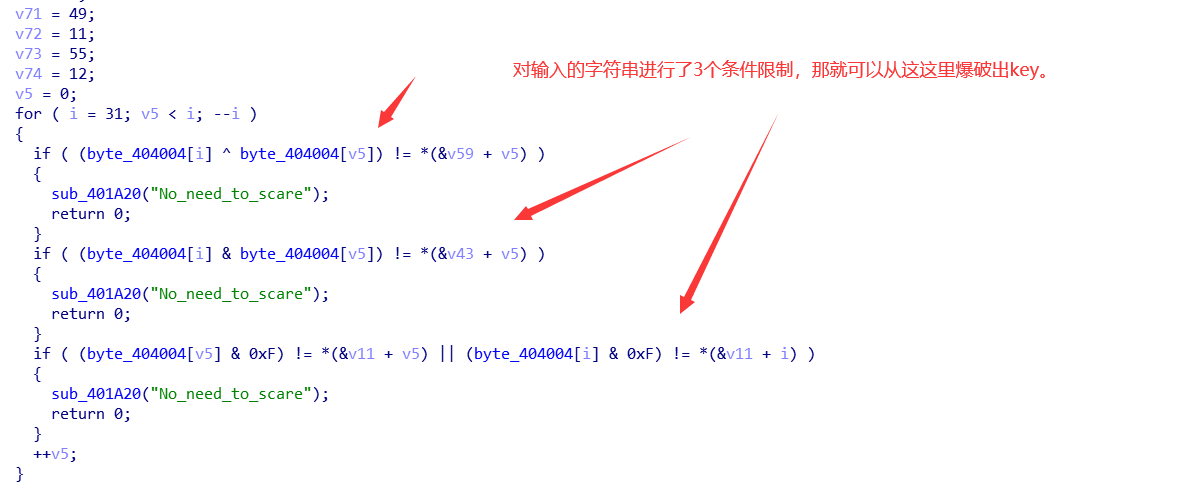
用限制条件写爆破试试:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
int main(void)
{
int i = 0, j = 0, k = 0, v5 = 0, y = 0;
char flag[33] = {0}, temp = 0;
char v11[] = {14, 5, 0, 11, 13, 9, 2, 3, 12, 5, 15, 1, 14, 4, 15, 13, 1, 8, 15, 15, 9, 3, 15, 14, 15, 4, 15, 6, 2, 5, 5, 13};
char v43[] = {76, 101, 96, 114, 100, 73, 112, 99, 108, 69, 83, 97, 78, 100, 72, 97};
char v59[] = {51, 0, 21, 9, 11, 54, 6, 12, 2, 58, 44, 8, 49, 11, 55, 12};
for(i = 31; i > v5; i--)
{
for(j = 33; j < 127; j++)
{
if((j & 0xf) == v11[i])
for(k = 33; k < 127; k++)
{
if((k & 0xf) == v11[v5])
{
if((k^j) == v59[v5] && (k&j) == v43[v5])
{
flag[i] = j, flag[v5] = k;
}
}
}
}
v5++;
}
puts(flag);
return 0;
}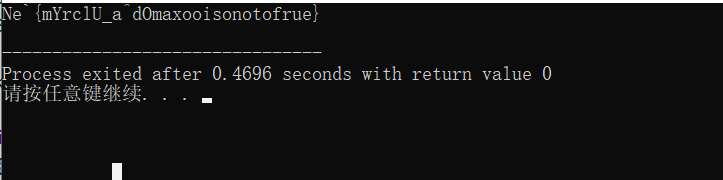
可以看到,情况是不唯一的,不然开始就会是Nep了。先接着往下看看:
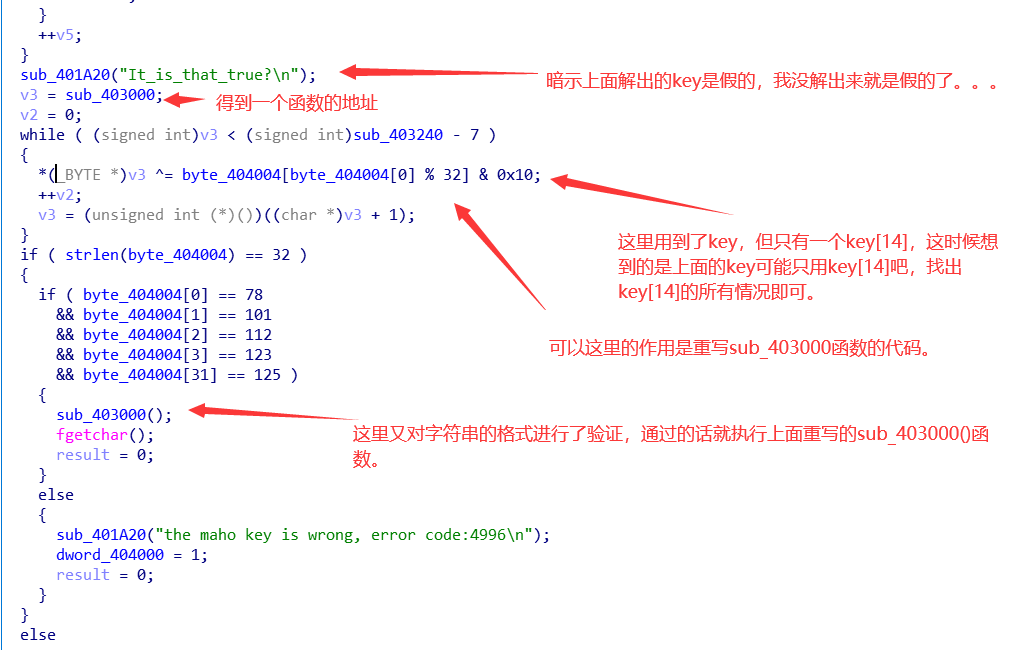
开始找重写的sub_403000()函数。先得到key[14]的所有情况:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
int main(void)
{
int i = 0, j = 0;
char v11[] = {14, 5, 0, 11, 13, 9, 2, 3, 12, 5, 15, 1, 14, 4, 15, 13, 1, 8, 15, 15, 9, 3, 15, 14, 15, 4, 15, 6, 2, 5, 5, 13};
char v43[] = {76, 101, 96, 114, 100, 73, 112, 99, 108, 69, 83, 97, 78, 100, 72, 97};
char v59[] = {51, 0, 21, 9, 11, 54, 6, 12, 2, 58, 44, 8, 49, 11, 55, 12};
for(i = 32; i < 127; i++)
{
if((i&0xf) == v11[14])
for(j = 32; j < 127; j++)
{
if((j&0xf) == v11[31-14])
{
if(((i^j) == v59[14]) && ((i&j) == v43[14]))
printf("%c%c ", i, j);
}
}
}
return 0;
}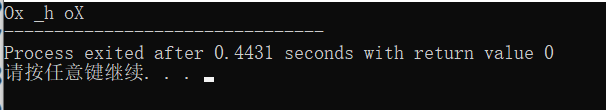
因为是成对的,将之前的得到的不唯一的key,指定位置换成这3对字符。然后载入OD,依次试一下,发现当Ox与oX都会报错,而_h正常执行。得到此时的程序状态后dump出来。
将dump出的文件,载入ida看一下重写的函数的功能。
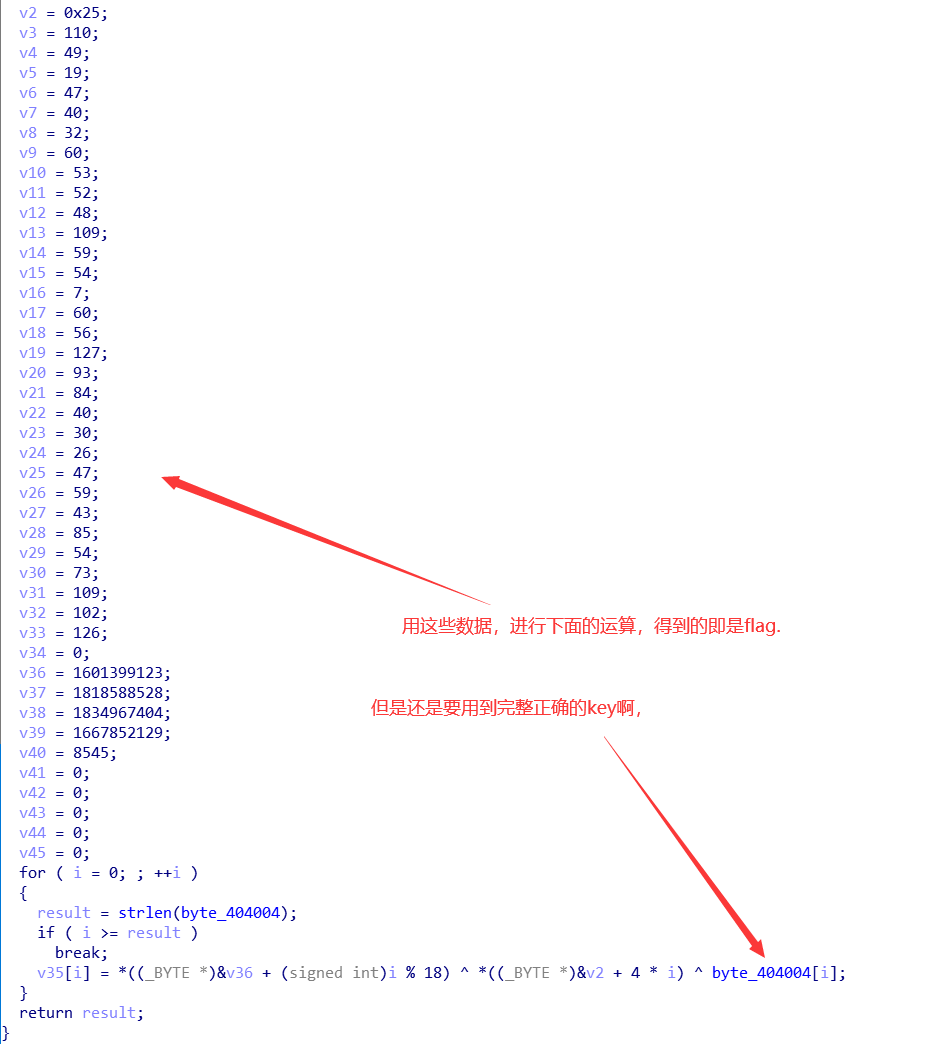
因为没看题目提示,使用之前找key[14]的办法,所有情况解出后看key怎么顺眼。最后得到:Nep{mircle_and_maho_is_not_free}
其实题目给了格式的提示。。。
再记录下ida中v35[i] = ……语句的地址,进入OD中下断点,然后输入正确的key,得到最终flag:
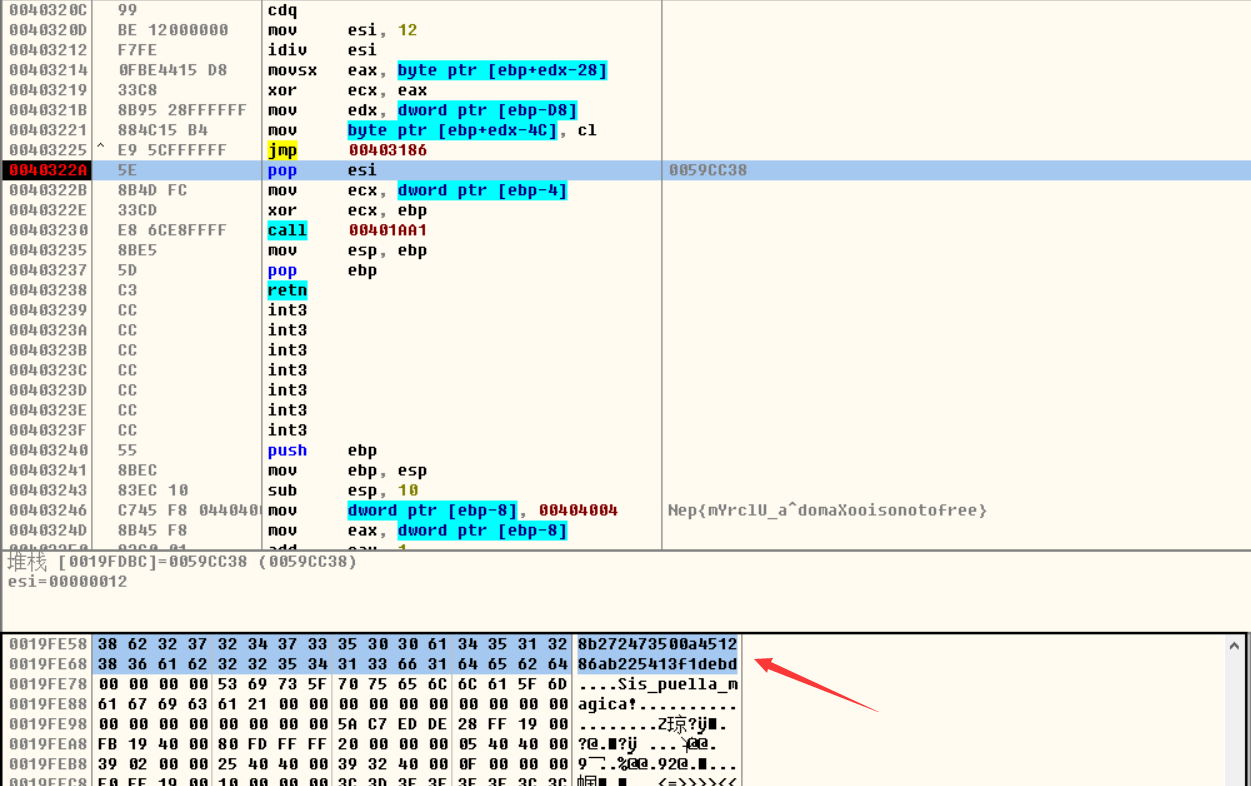
521
64位elf文件,运行看一下,直接让输入flag然后验证。
还是载入ida:
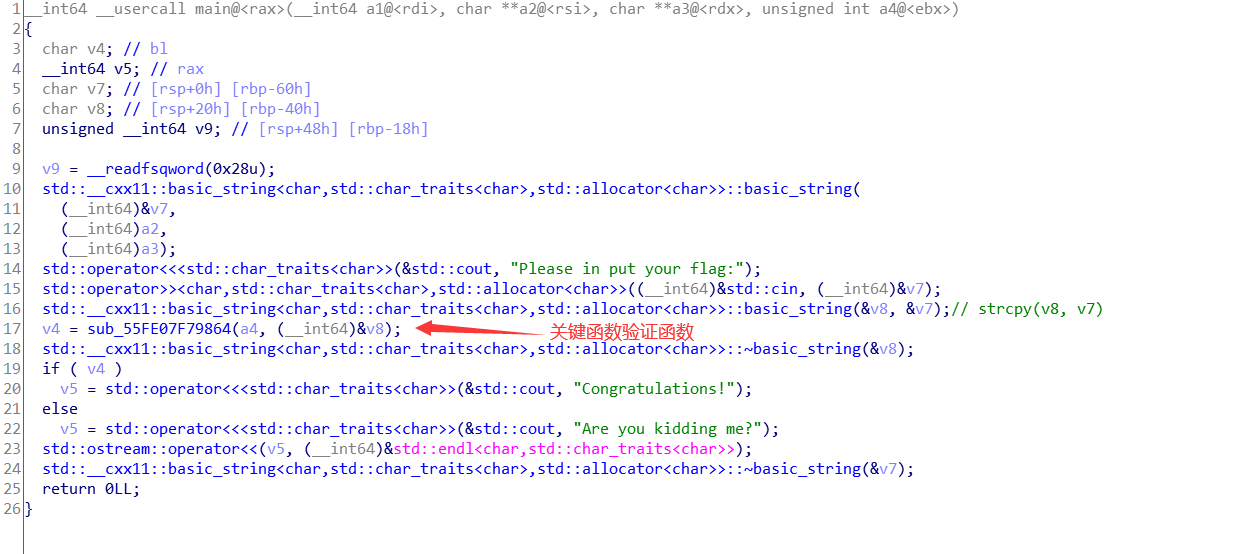
进入v4 = sub_55FE07F79864(a4, (__int64)&v8):
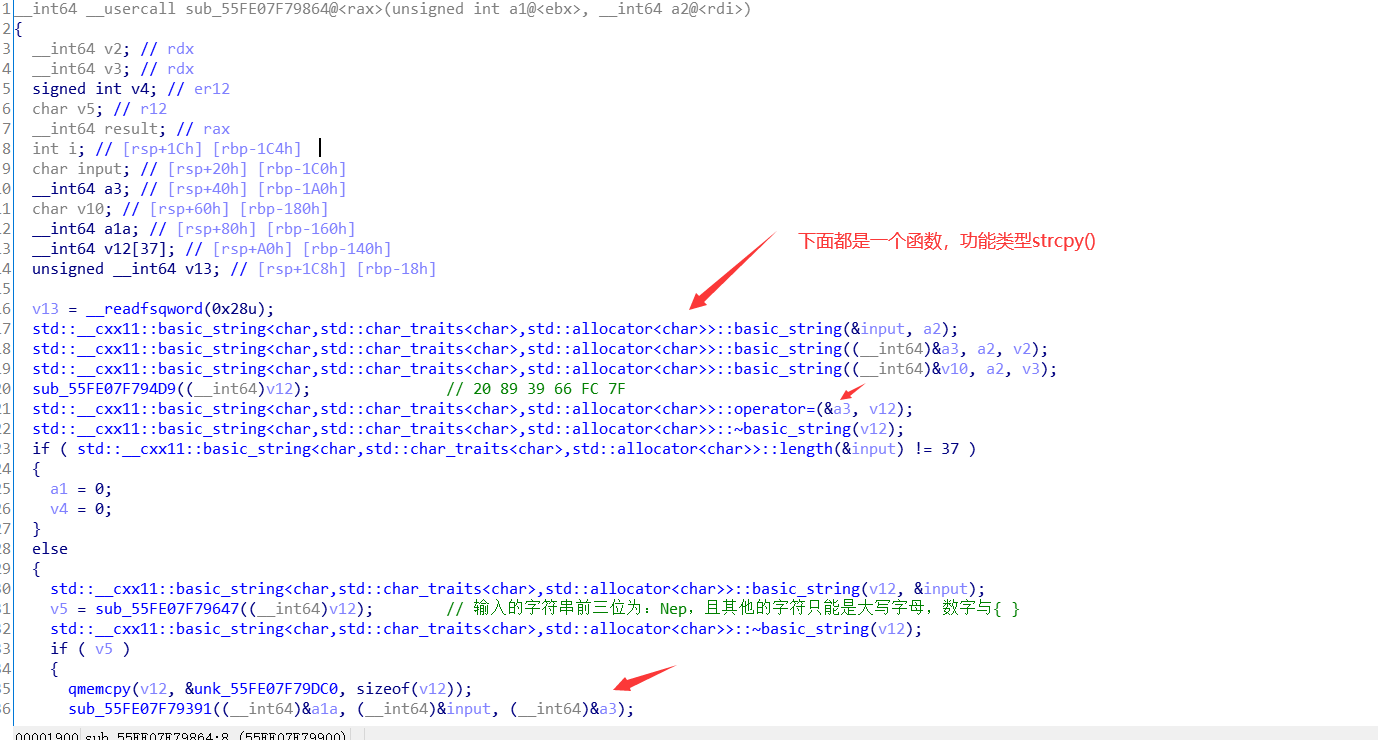
接着看下面:
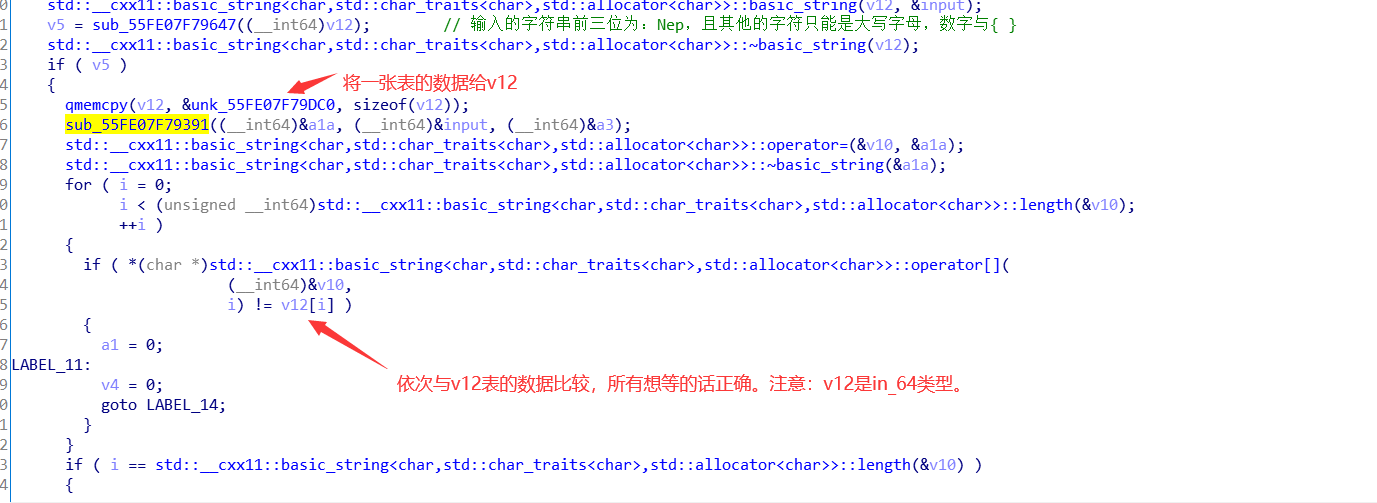
上面标黄的是整个题的关键函数,进入:
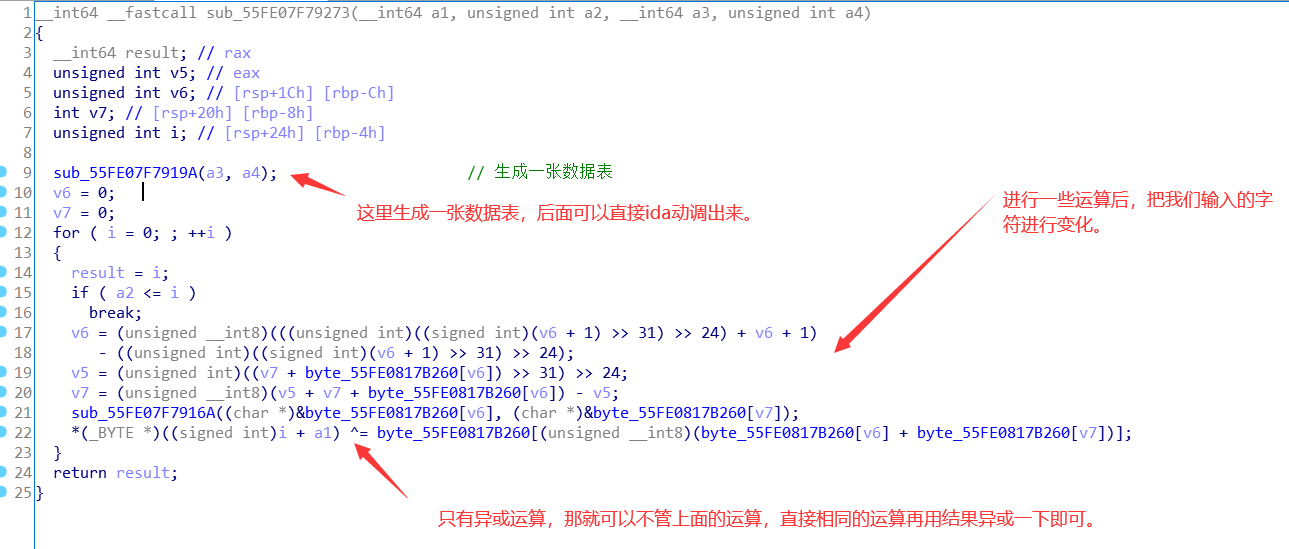
ida动调提取出数据表:
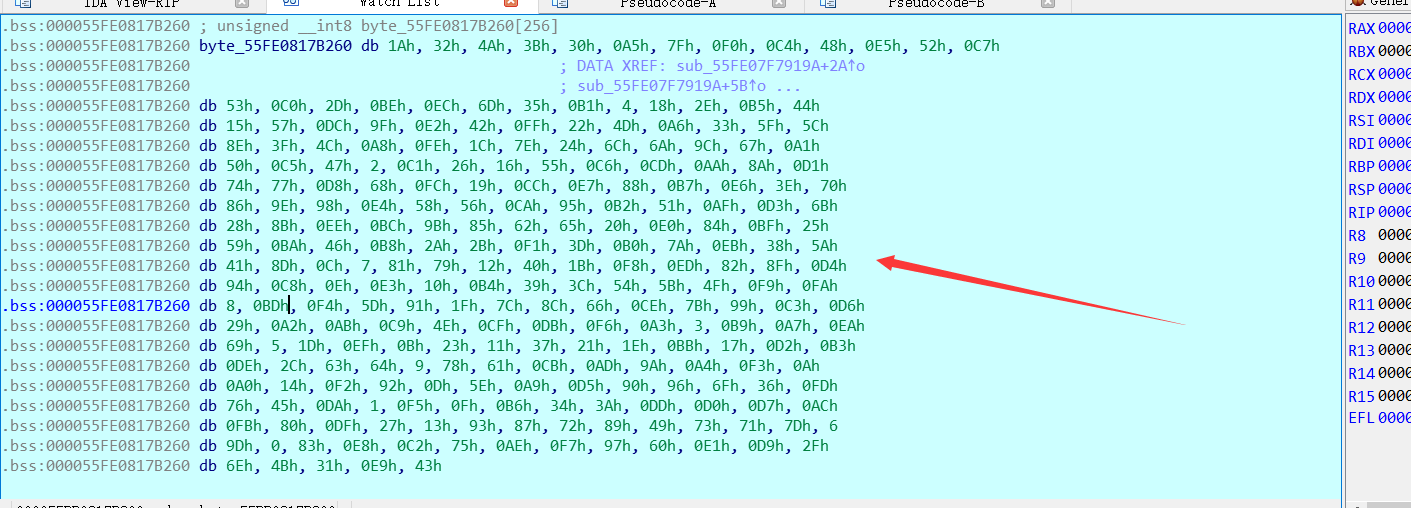
最后exp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
int main(void)
{
unsigned char ida_chars[] =
{
128, 255, 255, 255, 255, 255, 255, 255, 89, 0,
0, 0, 0, 0, 0, 0, 35, 0, 0, 0,
0, 0, 0, 0, 53, 0, 0, 0, 0, 0,
0, 0, 34, 0, 0, 0, 0, 0, 0, 0,
115, 0, 0, 0, 0, 0, 0, 0, 141, 255,
255, 255, 255, 255, 255, 255, 26, 0, 0, 0,
0, 0, 0, 0, 81, 0, 0, 0, 0, 0,
0, 0, 93, 0, 0, 0, 0, 0, 0, 0,
48, 0, 0, 0, 0, 0, 0, 0, 232, 255,
255, 255, 255, 255, 255, 255, 87, 0, 0, 0,
0, 0, 0, 0, 38, 0, 0, 0, 0, 0,
0, 0, 246, 255, 255, 255, 255, 255, 255, 255,
7, 0, 0, 0, 0, 0, 0, 0, 198, 255,
255, 255, 255, 255, 255, 255, 146, 255, 255, 255,
255, 255, 255, 255, 94, 0, 0, 0, 0, 0,
0, 0, 220, 255, 255, 255, 255, 255, 255, 255,
131, 255, 255, 255, 255, 255, 255, 255, 31, 0,
0, 0, 0, 0, 0, 0, 118, 0, 0, 0,
0, 0, 0, 0, 146, 255, 255, 255, 255, 255,
255, 255, 37, 0, 0, 0, 0, 0, 0, 0,
15, 0, 0, 0, 0, 0, 0, 0, 101, 0,
0, 0, 0, 0, 0, 0, 251, 255, 255, 255,
255, 255, 255, 255, 46, 0, 0, 0, 0, 0,
0, 0, 77, 0, 0, 0, 0, 0, 0, 0,
107, 0, 0, 0, 0, 0, 0, 0, 69, 0,
0, 0, 0, 0, 0, 0, 3, 0, 0, 0,
0, 0, 0, 0, 135, 255, 255, 255, 255, 255,
255, 255, 233, 255, 255, 255, 255, 255, 255, 255,
159, 255, 255, 255, 255, 255, 255, 255, 34, 0,
0, 0, 0, 0, 0, 0
};
unsigned char a[256] = {
0x1A, 0x32, 0x4A, 0x3B, 0x30, 0xA5, 0x7F, 0xF0, 0xC4, 0x48,
0xE5, 0x52, 0xC7, 0x53, 0xC0, 0x2D, 0xBE, 0xEC, 0x6D, 0x35,
0xB1, 0x04, 0x18, 0x2E, 0xB5, 0x44, 0x15, 0x57, 0xDC, 0x9F,
0xE2, 0x42, 0xFF, 0x22, 0x4D, 0xA6, 0x33, 0x5F, 0x5C, 0x8E,
0x3F, 0x4C, 0xA8, 0xFE, 0x1C, 0x7E, 0x24, 0x6C, 0x6A, 0x9C,
0x67, 0xA1, 0x50, 0xC5, 0x47, 0x02, 0xC1, 0x26, 0x16, 0x55,
0xC6, 0xCD, 0xAA, 0x8A, 0xD1, 0x74, 0x77, 0xD8, 0x68, 0xFC,
0x19, 0xCC, 0xE7, 0x88, 0xB7, 0xE6, 0x3E, 0x70, 0x86, 0x9E,
0x98, 0xE4, 0x58, 0x56, 0xCA, 0x95, 0xB2, 0x51, 0xAF, 0xD3,
0x6B, 0x28, 0x8B, 0xEE, 0xBC, 0x9B, 0x85, 0x62, 0x65, 0x20,
0xE0, 0x84, 0xBF, 0x25, 0x59, 0xBA, 0x46, 0xB8, 0x2A, 0x2B,
0xF1, 0x3D, 0xB0, 0x7A, 0xEB, 0x38, 0x5A, 0x41, 0x8D, 0x0C,
0x07, 0x81, 0x79, 0x12, 0x40, 0x1B, 0xF8, 0xED, 0x82, 0x8F,
0xD4, 0x94, 0xC8, 0x0E, 0xE3, 0x10, 0xB4, 0x39, 0x3C, 0x54,
0x5B, 0x4F, 0xF9, 0xFA, 0x08, 0xBD, 0xF4, 0x5D, 0x91, 0x1F,
0x7C, 0x8C, 0x66, 0xCE, 0x7B, 0x99, 0xC3, 0xD6, 0x29, 0xA2,
0xAB, 0xC9, 0x4E, 0xCF, 0xDB, 0xF6, 0xA3, 0x03, 0xB9, 0xA7,
0xEA, 0x69, 0x05, 0x1D, 0xEF, 0x0B, 0x23, 0x11, 0x37, 0x21,
0x1E, 0xBB, 0x17, 0xD2, 0xB3, 0xDE, 0x2C, 0x63, 0x64, 0x09,
0x78, 0x61, 0xCB, 0xAD, 0x9A, 0xA4, 0xF3, 0x0A, 0xA0, 0x14,
0xF2, 0x92, 0x0D, 0x5E, 0xA9, 0xD5, 0x90, 0x96, 0x6F, 0x36,
0xFD, 0x76, 0x45, 0xDA, 0x01, 0xF5, 0x0F, 0xB6, 0x34, 0x3A,
0xDD, 0xD0, 0xD7, 0xAC, 0xFB, 0x80, 0xDF, 0x27, 0x13, 0x93,
0x87, 0x72, 0x89, 0x49, 0x73, 0x71, 0x7D, 0x06, 0x9D, 0x00,
0x83, 0xE8, 0xC2, 0x75, 0xAE, 0xF7, 0x97, 0x60, 0xE1, 0xD9,
0x2F, 0x6E, 0x4B, 0x31, 0xE9, 0x43
};
int i = 0, v6 = 0, v7 = 0, v5 = 0, ans[37] = {0}, j = 0;
char flag[37] = {0};
for(i = 0; i < 296; i += 8)
{
ans[j++] = *(long int *)(&ida_chars[i]);
}
for(i = 0; i < 37; i++)
{
v6 = (unsigned char)(((unsigned int)((signed int)(v6 + 1) >> 31) >> 24) + v6 + 1) - ((unsigned int)((signed int)(v6 + 1) >> 31) >> 24);
v5 = (unsigned int)((v7 + a[v6]) >> 31) >> 24;
v7 = (unsigned char)(v5 + v7 + a[v6]) - v5;
int temp = a[v6];
a[v6] = a[v7];
a[v7] = temp;
flag[i] = ans[i]^a[(unsigned char)(a[v6] + a[v7])];
}
puts(flag);
return 0;
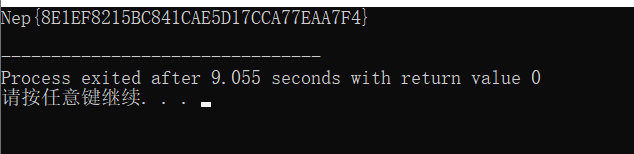
}
Misc
透明度
题目描述:你知道RGBA吗?
下载后是一张表情包。

从题目的描述与RGB有关,放入Stegsolve中看一下,可以看到在透明的管道隐藏有数据。且题目名称都是透明度。
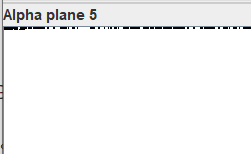
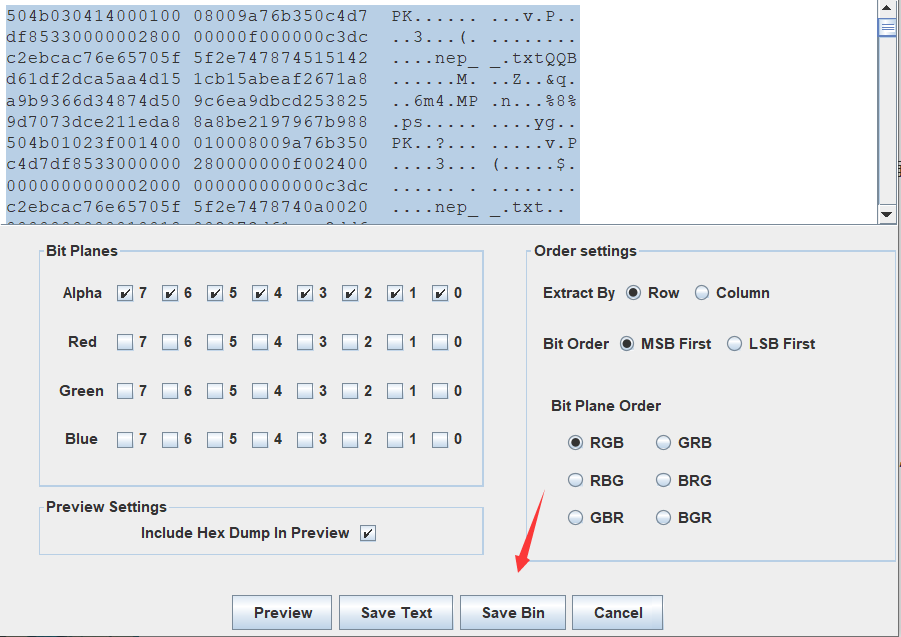
然后直接提取出透明管道的所有数据,但开始自己复制的数据然后粘贴到一个文件,最后得到的压缩包一直损坏。后面对比发现是每次换行的地方会出问题。
其实直接save bin 啊
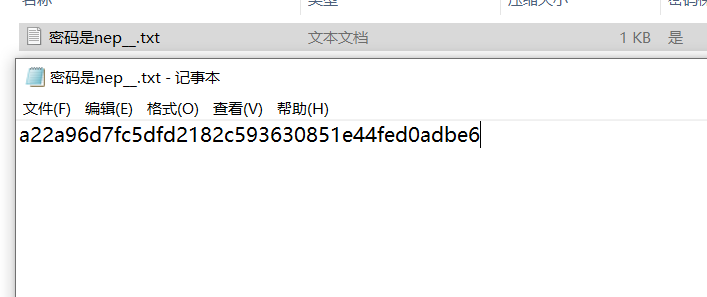
最后得到的要压缩包根据提示爆破出密码即可:nepnb
最后其实这个的题使用zesteg可以直接得到压缩包。
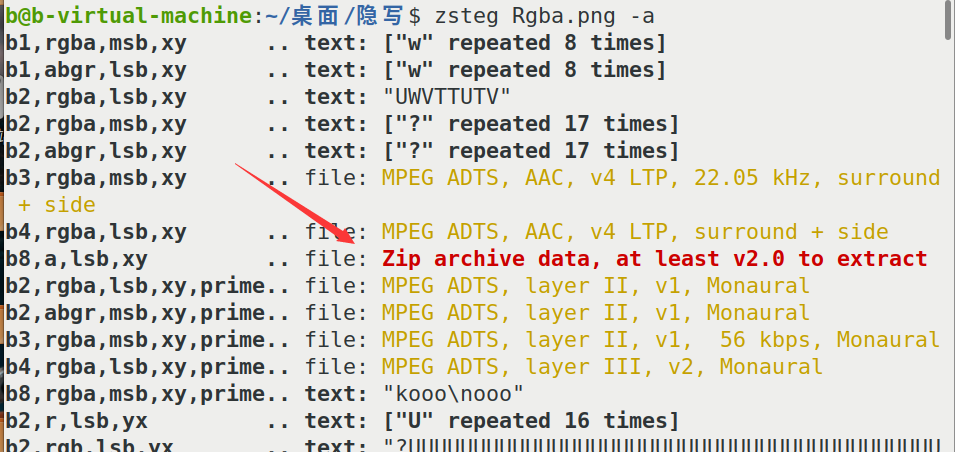
再使用zsteg Rgba.png -e ‘b8,a,lsb,xy’ > 1.zip提取出压缩包。